Design Steps
The Design steps for transaction mapping are same and in some cases identical to steps for transform mapping. The major dissimilarity lies in the mapping of the Data Flow Design to software structure.
Step 1: Reviewing the fundamental system model.
Step 2: Refine and Review data flow diagrams for the software.
Step 3: Determine whether the Data Flow Diagram has transaction or transform flow characteristics. By Steps 1, 2 and 3 are identical to corresponding steps in transform mapping. The Data Flow Design described in figure has a classic transaction flow characteristic. Moreover, flow behind 2 of the action paths emanating from the invoke command processing bubble appears to have transform flow characteristics. Thus, flow boundaries must be developed for both flow category.
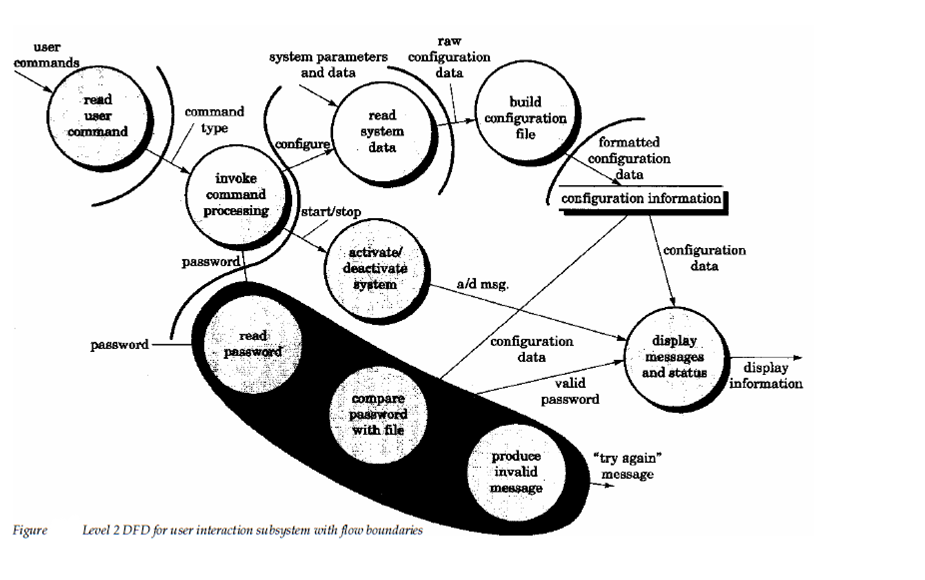
Step 4: Identify the transaction center and the flow characteristics along each of the action paths. The location of the transaction center can be immediately discerned from the Data Flow Design. Transaction center lies at the origin of a number of actions paths that flow radically from it. For the flow shown in figure the invoke command processing bubble is the transaction center.
The incoming path example for the flow path behind that a transaction is received and all action paths must also be isolated. The Boundaries which describe an action path and reception paths are also described in the figure. Each and every action path must be evaluated for is individual flow characteristic. Example for, the password path shown enclosed through a shaded area in figure has transform characteristics. Transform, Incoming and outgoing flow are indicated with boundaries.
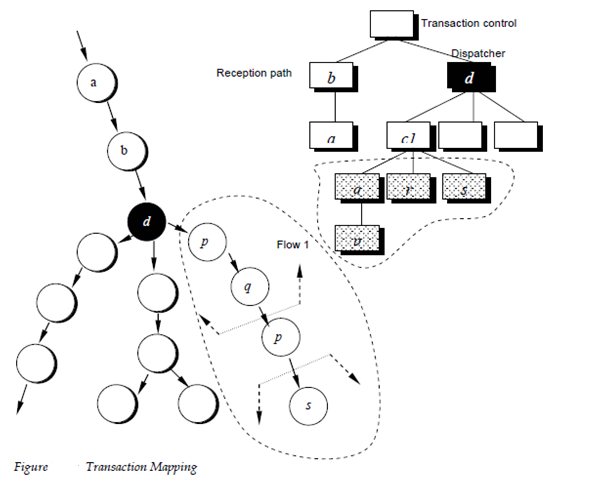
Step 5: Map the Data Flow Diagram in a program structure amenable to transaction processing. The Transaction flow is mapped into a program structure that contains an incoming branch and a dispatch branch. The Structure for the incoming branch is established in much the similar way as transform mapping. Begins at the transaction center, bubbles behind the incoming path are mapped into modules. Structure of the dispatch branch contains a dispatcher module which controls all subordinate action modules. Each and every action flow path of the Data Flow Diagram is mapped to a structure which corresponds to its exact flow characteristics. This procedure is described in figure 20.12.
By considering the user interaction subsystem data flow 1st level factoring for step 5 is describe in figure 20.13. The bubbles read user command and activate or deactivate system map directly into the program structure without the requirement for intermediate control modules. The invoke command processing, transaction center, maps directly into a dispatcher module of the similar name.Controllers for system password and configuration processing are mapped as demonstrate in figure 20.12.
Step 6: Factor and refine the transaction structure and the structure of each action path. Each and every action path of the data flow diagram has its own information flow characteristics. We have already noted which transform or transaction flow may be encountered. The action path-related substructure is established using the design steps discussed in this and the preceding section.
As an example let’s consider the password processing information flow described inside shaded field. The flow exhibits classic transform characteristics.The password is input transmitted and incoming flow to a transform center where it is compared against stored passwords.A warning and alarm message outgoing flow are produce if a match is not obtained. The configure path is drawn same using the transform mapping. The resultant program structure is described in figure
Step 7: Refine the first iteration program structure using design heuristics for improved software quality. The 7th step for transaction mapping is identical to the corresponding step for transform mapping. In the both design approaches and criteria such as module practicality, efficacy, independence of implementation and test and maintainability must be carefully considered as structural modifications are proposed.