Safe Home Privacy System
To describe the use of these basic guidelines the safe home privacy system example is discussed in past lecture. The processing narrative for safe home is reproduced given below:
The Safe Home software enables the homeowner to configure the security system when it is installed monitors all sensors connected to the security system and interacts with the homeowner by a function and keypad keys contained in the Safe Home control panel.
In the duration of installation the Safe Home control panel is used to configure and program the system. Every sensor is assigned a number and kind a master password in programmed for disarming and arming the system and telephone numbers are input for dialing when a sensor moment happen.
When a sensor event is acknowledge the software invokes an audible alarm attached to the system. Then a delay time which is specified through the homeowner during system configuration activities the software dials a telephone number of monitoring service gives information about the location, reporting and the nature of the event which has been detected. Telephone number will be redialed every twenty seconds until telephone connection is obtained.
All the interaction with Safe Home is managed through a user-interaction subsystem which reds input provided by the keypad and function keys display prompting system and messages status on the LCD display. The Keyboard interaction takes the following form...
Discussing among the customer and the analyst indicate the following list of things which are relevant to the problem.
- Homeowner
- Control panel
- Sensors
- Security system
- Monitoring service
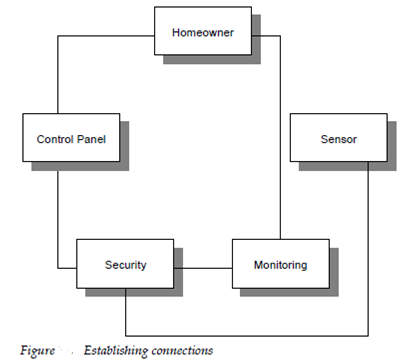
By taking these things 1 at a time connections are explored. To accomplish this every object is drawn and lines connecting the objects are noted. Example for, in the figure 16.6 shows in which a direct connection exists among the control panel and homeowner, security system, and monitoring service. The single connection exists among security and sensor system, and so 4th.
Once all connections have been described, one or more object relationship pairs are identified for each and every connection. Example for, the connection among security and sensor system is determined to have the following object relationship pairs.
Security system monitors sensors
Security system enables or disables sensor Security system tests sensor
Security system programs sensor
Each of the above object relationship pairs is analyzed to determine modality and cardinality. Example for in the object relationship pair security system monitors sensor the cardinality among security system and sensor is one too many. Modality is one occurrence of security system and at least one occurrence of sensor. By using the ERD notation introduced the connecting line among security system and sensor would be modified which is shown in figure 16.7 same analyses would be applied to all other data objects.
Every object is studied to determine its attributes. Still we are considering the software that mist support Safe Home the attributes should focus on data in which a must be stored to enable the system to operate. Example for, the sensor object might have the following attributes that are: internal identification number, sensor type, alarm level and Zone location.