What are the various states through which a transaction passes through in its lifetime? Briefly discuss all the events that causes transition from one state to another.
Ans: A transaction can be referred to be an atomic operation by the user, but in fact it goes through a number of states during its lifetime as given as follows:
a. Active, the initial state; the transaction stays in this state when it is executing
b. Partially Committed, later than the initial statement has been executed
c. Failed, later than the discovery that normal execution can no longer proceed
d. Aborted, later than the transaction has been rolled back and the database has been restored to its state prior to the beginning of the transaction
e. Committed, after successful completion.
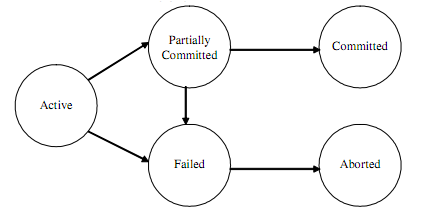
It is supposed that before a transaction starts, the database is in a consistent state. A transaction starts while the first statement of the transaction is executed; it becomes active. Afterward any outcome, the database will be referred in consistent state.