Q. Consider the specification written below of a graph G
V(G ) = {1,2,3,4}
E(G ) = {(1,2), (1,3), (3,3), (3,4), (4,1)}
(i) Draw the undirected graph.
(ii) Also draw its adjacency matrix.
Ans:
V(G) = {1,2,3,4}
E(G) = {(1,2),(1,3),(3,3,),(3,4),(4,1)}
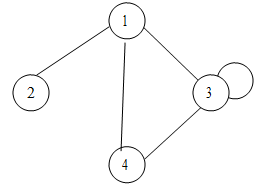
(i). The undirected graph is shown as follows:-
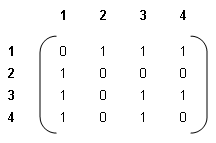
(ii) The adjacency matrix is written as follows:-