As we already seen that the scaling process is mainly utilized to change the size of an object. The scale factors find out whether the scaling is a magnification as s>1 or a reduction, s<1. 2-dimensional scaling, is in equation (8), can be simply extended to scaling in 3-dimensional case by consisting the z-dimension.
For any point (x,y,z), we move in (x.sx,y.sy,z.sz), here sx, sy, and sz are the scaling factors in the x,y, and z-directions correspondingly.
Hence, scaling w.r.t. origin is given by:
Ssx,sy,sz = x'= x.sx
y'= y.sy
z'= z.sz---------(43)
In matrix form:
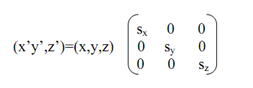 ------------------------(44)
------------------------(44)
In terms of Homogeneous coordinate system, above equation (44) is written as:
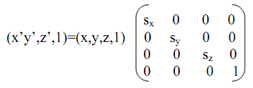
As, P'=P. Ssx,sy,sz -----------------------------(45)