Z-Buffer Algorithm
Also known as the Depth-Buffer algorithm, this image-space method simply selects for display the polygon or portion of a polygon that is nearest to the viewer, by checking the z-value of every pixel. Let us consider the quadrilateral ABCD of Figure, with the triangle EFG in front of it, and rectangle : PQRS behind it.
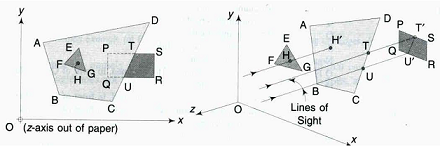
As shown in Figure, for any point H in the triangle, its projection H′ on the quadrilateral will be behind H, and ZH will be less than ZH′. Hence, the entire triangle EFG will be visible.
On the other hand, the rectangle PQRS is partially hidden by the quadrilateral, the portion PQUT being hidden and the portion TURS being visible. This will be mathematically known by the fact that for all points (x, y) within the region PQUT, the Z for the quadrilateral will be less than the Z for the rectangle, while for all points within the region TURS, there will be no common (x, y) between the quadrilateral and the rectangle, leaving only the rectangle portion to be visible. The rays for the determination of H ′, T, and U ′ from H, T, and U are shown in parallel projection in Figure(b). The z-buffer memory size by this method is only dependent on the viewport, and any number of polygons can be handled.