Speed Up:-
Speed up is the ratio of the time required to implement a given program using a definite algorithm on a machine with one processor (i.e. T (1) (where n=1)) to the time required Advanced Topics to implement the similar program using a specific algorithm on a machine with multiple processors (i.e. T(n)). Basically the speed up factor helps us in knowing the relative gain achieved in shifting from a sequential machine to a parallel computer. It may be noted that the term T(1) signifies the amount of time taken to implement a program using the best sequential algorithm i.e., the algorithm by least time complexity
S(n) = T(1) T(n).
Let us take an example and illustrate the practical use of speedup. Assume, we have a problem of multiplying of n numbers. The time complexity of the sequential algorithm for a machine with one processor is O (n) as we require one loop for reading as well as computing the output. Though, in the parallel computer, let each number be allocated to individual processor and computation model being used being a hypercube. In such a Condition, the total number of steps needs to compute the result is log n i.e. the time complexity is O(log n). Figure, illustrates the steps to be followed for achieving the desired output in a parallel hypercube computer model.
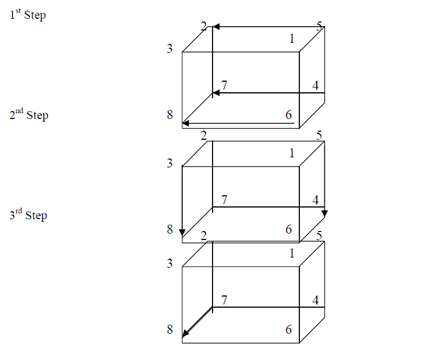
Steps followed for multiplying n numbers stored on n processors
As the number of steps followed is equal to 3 i.e., log 8 where n is number of processors. Therefore, the complexity is O(log n).
In view of the fact that sequential algorithm takes 8 steps and the above-mentioned parallel algorithm takes 3 steps, the speed up is as beneath:
S (n) = 8/3
As the value of S(n) is inversely proportional to the time necessary to compute the output on a parallel number which in turn is dependent on number of processors employed for performing the computation. The relation among S (n) vs. Number of processors is shown in Figure. The speeadup is directly proportional to number of processors, thus a linear arc is depicted. Though, in situations where there is parallel overhead, the arc is sub-linear.
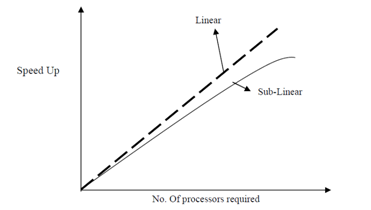
Speed-up vs. Number of Processors