The combinational circuits use the comparators for comparing the storing and number them on the basis of minimum and maximum functions. Likewise, in the interconnection networks the two processors perform the computation of minimum and maximum functions in the following way:
Let us consider there are two processors pj and pi. Each of these processors has been given as input a part of the sequence, say ej and ei. Now, the processor pi sends the element ei to pj and processor pj sends ej to pi. After that, processor pi determine the minimum of ei and ej i.e., min (ei,ej) and processor pj determine the maximum of ei and ej, i.e. max (ei,ej). The above method is called as compare-exchange and it has been depicted in the Figure .
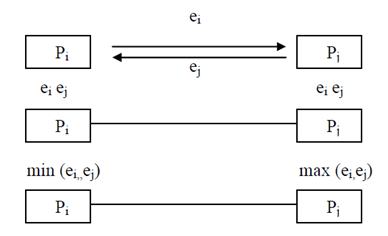
Illustration of Exchange-cum-Comparison in interconnection networks
The sorting problem chosen is bubble sort and the interconnection network can be depicted as n processors interconnected with each other in the type of a linear array as given in Figure. The method adopted for solving the bubble sort is called as odd- even transposition. Suppose an input series is B=(b1, b2, b3, b4......... bn) and each number is assigned to a particular processor. In the odd-even transposition,the sorting is executed with the help of two phases known as odd phase and even phase. In the odd phase, the elements stored in (p1, p2), (p3, p4), (p5, p6)......... (pn-1, pn) are compared according to the Figure and consequently exchanged if required i.e. if they are out of sort. In the even phase, the elements stored in (p2, p3), (p4, p5), (p6, p7)......... (pn-2, pn-1) are compared according to the Figure and consequently exchanged if required, i.e. if they are out of order. keep in mind, in the even phase the elements stored in p1 and pn are not exchanged and compared. The total number of phases needed for sorting the numbers is n i.e. n/2 odd phases and n/2 even phases. The algorithmic representation of the above discussed odd- even transposition is given below:
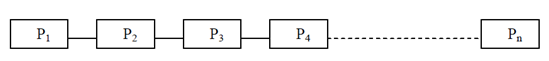
Interconnection network in the form of a Linear Array