The 68HC11 series is based on the Motorola 6800/1 programming instruction set and hence is a fairly simple 8 bit microprocessor. The internal structure of the 6800/1 is shown below
The 6800/1 contains two 8 bit accumulators namely A,B which are used to process/hold data for the Arithmetic/Logic calculations . These can be combined to form one single 16 bit accumulator namely D. Also included are two 16 bits index register IX, IY which are mainly used for pointing too addresses , but can also be used as a 16 bit store or counter. The next two 16 bits registers are the Program counter (PC) used for holding the current address of the program and the stack pointer (SP) used for holding the address of the next available stack (RAM) position .The final register is a 8 bit register called the condition code register (CCR) , this is used to hold the results of the last ALU operation , each bit (flag) is a particular ALU condition as shown below
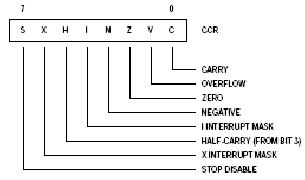
C- Carry/Borrow flag if set indicates that an arithmetic carry/borrow has occurred
V overflow if set indicates that the answer was greater that 8 bits
Z zero flag if set if the ALU answer has produced a zero
N - Negative if set this indicates that a negative number has been generated i.e. bit 7 = 1
I - Interrupt mask if set stops further masked interrupts from happening
H Half carry, if set indicates that a half carry has occurred i.e. ALU result has caused a carry to occur between bit 3,4
X - Interrupt mask, if set indicates that a non masked interrupt has occurred i.e. Reset or XIRQ. Cleared by TAP or RTI
S Stop disable if set disables the use of the stop instruction, if cleared enables the stop command
The 68HC11 instruction set consists of three major groups:
Maths Functions
Movement functions
Processor commands
Before we tackle each section we shall first discuss the various addressing modes of each instruction