Q. Show the Network layer in an internetwork?
- Receives data from Transport layer
- Responsible for creating Packet
- Each packet contains
- Universal Address of Source
- Universal Address of Destination
- Makes sure the pkt is correct size.
- If the packet is too large,
- Then it will be fragmented
- Also add fields for error control
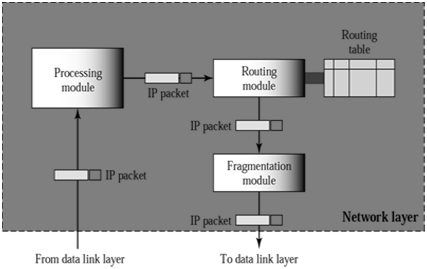
Figure Network layer at a Router
- Responsible for routing the packet
- When packet arrives, router finds the interface from which the pkt must be sent.
- This is done by utilizing routing Table.
- If necessary, perform fragmentation
Network layer at the destination
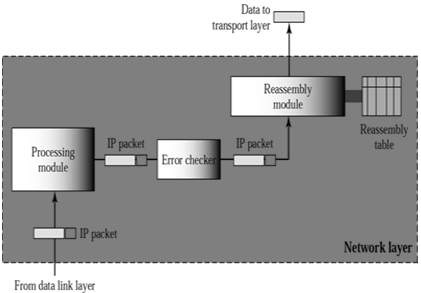
- Responsible for Address Verification.
- Ensure the destination is correct.
- As well checks to see the packet has been corrupted during transmission.
- If corrupted then discards the packet.
- If the packet is fragment, it waits all fragments have arrived