Reliable Data Transfer
Figure illustrate the framework for reliable transfer. The service abstraction provided to the upper layer entities is that of a reliable channel through which data can be transferred. With a reliable channel no transferred data bits are corrupted ( flipped from o to 1or vice versa) or lost and all are delivered in the order in which they were sent. This is precisely the service model offered by TCP to the internet application that invoke it.
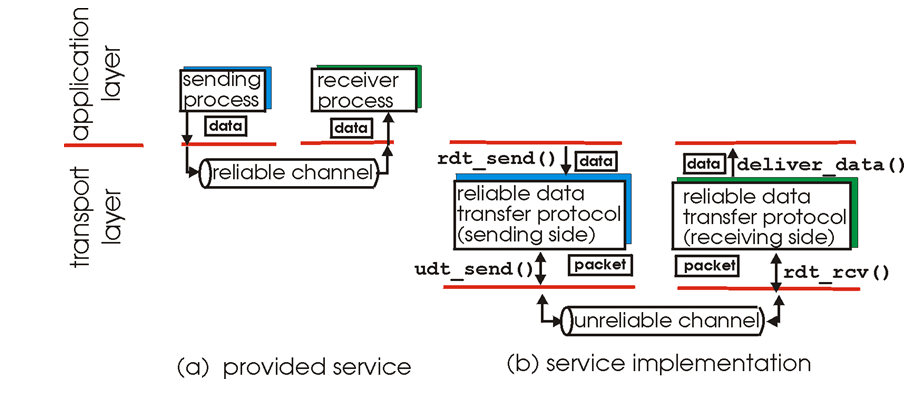
Figure Reliable data transfer: Service model service implementation
It is the responsibility of a reliable data transfer protocol to implement this servers abstraction. This task is made difficult by the fact that the layer below the reliable data transfer protocol may be unreliable. For example IP is a reliable data transfer protocols that is implemented on top of an unreliable IP end to end network layer.
In this section we will incrementally develop the sender and receiver sides of a reliable data transfer protocols, considering increasingly complex models of the underlying channel. Figure illustrates the interfaces for our data transfer protocols.
a.When the application wants to send data, it calls rdit send to activate teh transport protocols.
b.The transport protocols builds a packet and cells udt send to send to packet over the lower layer.
c.On the receiving side when the lower layer protocols has a packet to deliver it calls rdt rcv .
d.The transport protocols extracts the data from teh packet and delivers the data to the applications by calling deliver data.
e.This protocols is called rdt 1.0.