Q. Process of An e-mail transfer across the Internet?
When you open your mail client to read your e-mail, this is what normally happens:
1. Mail client (Netscape Mail, Microsoft Outlook, Lotus Notes etc.) opens a connection to its default mail server. Mail server's IP address or domain name is typically setup when mail client is installed.
2. Mail server will always transmit first message to identify itself.
3. Client will send an SMTP HELO command to which the server would respond with a 250 OK message.
4. Depending on whether client is checking mail, sending mail etc. the appropriate SMTP commands would be sent to the server, which will respond accordingly.
5. This response/request transaction will continue until the client sends an SMTP QUIT command. Server will then say goodbye and connection will be closed.
Likewise, when you send an e-mail message your computer sends it to an SMTP server. Server forwards it to the recipient's mail server depending on email address. Received message is stored at the destination mail server until addressee retrieves it. To receive E-mail a user Internet account includes an electronic mailbox. A message sent for you is received at your Internet host computer, where it is stored in your electronic mailbox. The instant you login into your Internet account, one of the first things you must do is to check your mailbox.
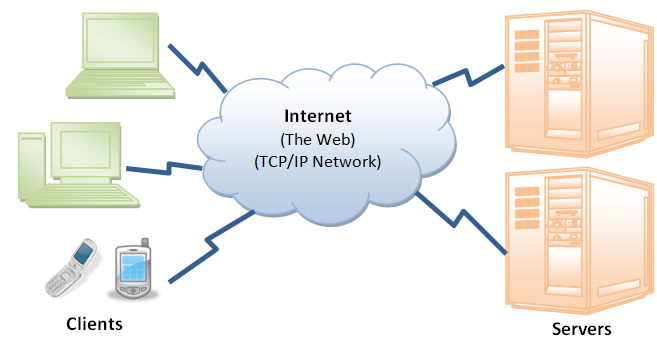
Figure: An e-mail transfer across the Internet uses two programs: client and server
E-mail system follows client-server approach to transfer messages across the Internet. When a user sends an E-mail message a program on the sender's computer becomes a client. It contacts an e-mail server program on recipient's computer and transfers a copy of message. Some of the mail programs those exist on Internet are UCB mail, Pine, Elm etc. Though, one thing, which you should emphasize when selecting a mail program, is user friendliness of that program. Through E-mail on Internet you can be in direct touch of your friend and colleagues.