Prepare the Network
Step 1: Disable all ports by using the shutdown command.
Ensure that the initial switch port states are inactive with the shutdown command. Use the interface-
range command to simplify this task.
S1(config)#interface range fa0/1-24
S1(config-if-range)#shutdown
S1(config-if-range)#interface range gi0/1-2
S1(config-if-range)#shutdown
S2(config)#interface range fa0/1-24
S2(config-if-range)#shutdown
S2(config-if-range)#interface range gi0/1-2
S2(config-if-range)#shutdown
S3(config)#interface range fa0/1-24
S3(config-if-range)#shutdown
S3(config-if-range)#interface range gi0/1-2
S3(config-if-range)#shutdown
Step 2: Re-enable the user ports on S1 and S2 in access mode.
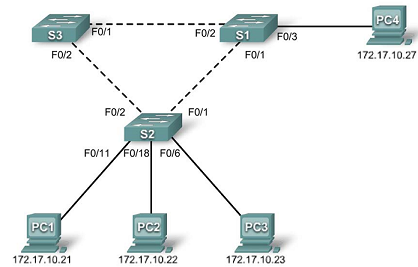
Refer to the topology diagram to determine which switch ports on S2 are activated for end-user device
access. These three ports will be configured for access mode and enabled with the no shutdown
command.
S1(config)#interface fa0/3
S1(config-if)#switchport mode access
S1(config-if)#no shutdown
S2(config)#interface range fa0/6, fa0/11, fa0/18
S2(config-if-range)#switchport mode access
S2(config-if-range)#no shutdown