Title: Perimeter Network Security System
Outline Requirements
The University is based in Glasgow, and provides higher education services to its students and staff. It is located on a single campus called Campus A. Students and staff use the network services from hosts on various different user networks, as shown in
Figure 1
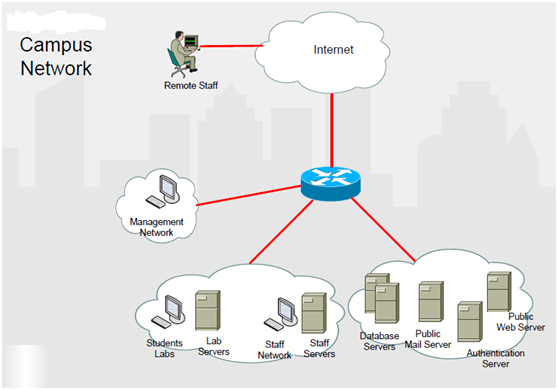
.
Due to an increasing number of security violations, a possible redesign of the network infrastructure is to be investigated. You have been hired as a consultant to propose security enhancements, and produce a report. The aim of the exercise is to present a possible solution to the problem at hand by creating a prototype of the new network security infrastructure. This new design should tackle the following components:
- Provide best practice network egress and ingress filtering at the network perimeter.
- Create a perimeter firewall, with an appropriate topology to provide the organisations services, including public web, and mail servers. The firewall should have a closed security stance, and provide public services in a secure way.
- Provide secure access to all devices, from the security management subnet.
Additionally, research should be carried out into increasingly common Advanced Persistent Threats (APT), and ways to defend against these using network defenses. This part of the coursework will be research only and be confined to a part of the Research Section.
You will be required to analyze the new system requirements and design, implement and justify a prototype for each component of the proposed system. Your proposed system can be implemented on Cisco hardware deployed in the network lab, or on the virtual networking software (such as GNS3). The system should clearly demonstrate your mastery of the course material. Each component of the system should be developed separately, and it is not necessary to implement an entire working system.
Marking schedule
Your coursework will be marked as follow
Introduction
Demonstrate an understanding of the problem specification, the challenges and research, design and implementation.
Research and Design
This should show an outline of the proposed system, and the main design features.
- Provide short literature review for each of the proposed key components(demonstrating research from a variety of sources, critical evaluation and personal reflection).
- Provide design of network security system components, and justify your decisions.
Prototype Implementation
This should define an outline prototype implementation of the system.
- Implement the key components of the proposed network system design (describe and show examples of your implementation including diagrams, as there will not bepractical demonstration).
Testing and Evaluation
This should show testing, and outline the results of any evaluations that you have made.
- Describe and demonstrate the testing methods used, and show the outcome of the testing.
- Include evaluation of the systems and technologies used, using references to the literature and personal reflection.
Conclusions
This should reflect the methods you have used in the report, and to assess their benefitsand limitations, and any observations that you have gained.
- Draw conclusions about the network security systems created, including conclusions about your design as well as the implementation.
- Any recommended future improvements, based on your findings.
References/Presentation
Full academic referencing of books, web sites, and papers, using thorough APA/Harvard referencing format.
- All references must be defined in an APA/Harvard format, and should be listed at the end of the report.
- Reference all materials used, and cite every reference in the body of the report.
· Total report size should be 15-20 pages that does not include cover page, and appendix - if any.
· The report should be in 11 point text with normal margins.
- the similarity must be below 7%. Numbers above 7% indicate a possible problem
- submition is through turnitin