Q. Operating System as User Interface?
• Every general purpose computer comprises the operating system, hardware, system programs and application programs. The hardware comprises CPU, ALU, Memory,I/O devices, peripheral device and storage device. System program comprises compilers, loaders, editors, OS etc. Application program comprises database program, business program.
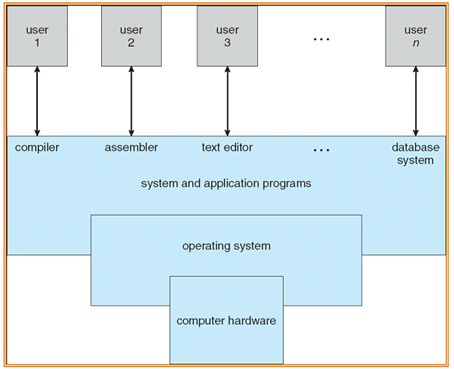
• Every computer should have an operating system to run other programs. Operating system and coordinates the use of hardware among numerous system programs and application program for various users. It simply offers an environment within that other programs can do useful work.
• Operating system is a set of special programs that run on a computer system which allow it to work properly. It performs basic tasks like recognizing input from the keyboard, keeping track of files and directories on the disk, sending output to display screen and controlling a peripheral devices.
• OS is designed to serve two fundamental purposes :
1. It controls the allocation as well as use of the computing system‘s resources among the various user and tasks.
2. It provides an interface between computer hardware and programmer which simplifies and makes feasible for coding, creation, debugging of application programs.
• The operating system should support the below tasks. The tasks are :
1. Provides facilities to create, modification of program as well as data files using an editor.
2. Access to the compiler for translating user program from high level language to machine language.
3. Provide a loader program to move compiled program code to computer‘s memory for execution.
4. Provide routines which handle the details of I/O programming.