Odd-Even Merging Circuit
Let's firstly understand the idea of merging two sorted sequences using an odd-even merging circuit. The functioning of a merging circuit is as given below:
1) Let there be 2 sorted sequences A= (a1, a2, a3, a4......... am) and B= (b1, b2, b3, b4......... bm) that are needed to be merged.
2) With help of a merging circuit (m/2, m/2) merge the odd indexed numbers of two sub sequences it implies that (a1, a3, a5......... am-1) and (b1, b3, b5......... bm-1) and so resulting in sorted sequence (c1, c2, c3......... cm).
3) Afterwards, with the help of a merging circuit (m/2, m/2) merge the even indexed numbers of the two sub sequences it implies that (a2, a4, a6......... am) and (b2, b4, b6......... bm) and so resulting in sorted sequence (d1, d2, d3......... dm).
4) The last output sequence O= (o1, o2, o3......... o2m) is attained in the given below manner: o1 = a1 and o2m = bm .In broad the formula is as following: o2i = min (ai+1, bi) and o2I+1 = max(ai+1,bi ) for i=1,2,3,4..........m-1.
Now let's take an illustration for merging the 2 sorted sequences of length 4 it implies that A= (a1, a2, a3, a4) and B= (b1, b2, b3, b4). Assume numbers of sequence are A= (4, 6, 9, 10) And B= (2, 7, 8, 12). The circuit of merging the two provided sequences is explained in Figure.
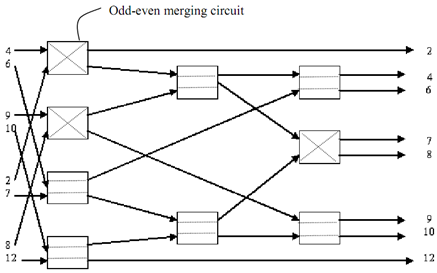
Figure: Merging Circuit