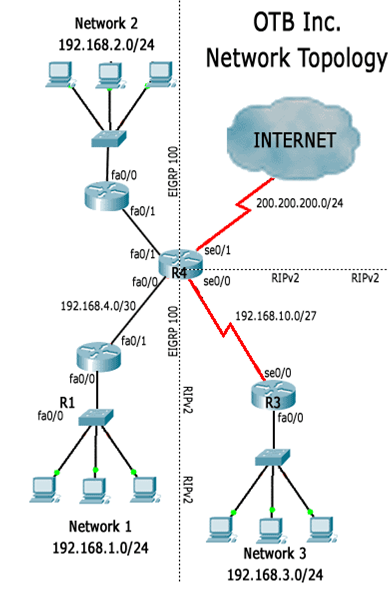
According to the report, network 1 and network 2 are not able to reach network 3. As shown on OTBNetwork Topology above, OTB Inc. has 2 routing protocols running due transition issues. The goal is tohave only one protocol running within the network but for now the older protocol must be kept. In order toachieve full connectivity, OTB routes generated by one routing protocol must be injected into the otherone.
Step 1 - Checking the routers
You connect to R3 via console port to check its configuration. R3 is a RIPv2 speaker and a quick look atits configuration does not show anything unexpected: RIPv2 is correctly configured at R3, all R3interfaces are up but R3 learned no routes via RIPv2.
Still from R3, you issue a few pings: pings to a few PCs under network 3 and to R4's serial 0/0 interfaceare successful. Pings to R2's interfaces and to R1's interfaces fail.
You also issue a few pings from a few PCs under network 3 towards a few PCs under network 1 but all ofsuch pings fail.
A quick look into R3's routing table reveals it has no default route or routes to the EIGRP side of OTB'snetwork. Since R3's configuration is correct, you assume some router was incorrectly configured andthus, wrongly advertising routes.
Since R3 is not learning routes from the EIGRP side, you decided to check EIGRP configuration into theEIGRP routers. You move to the EIGRP side, switch the console cable to R1 and check its configuration.
Once more, the configuration is correct: all R1's interfaces are up, EIGRP is correctly configured and R1has EIGRP routes installed into its routing table. R1 has a default route pointing to R4's fa0/0 which waslearnt via EIGRP from R4.
R1 also has EIGRP routes to network 3 (192.168.3.0/24). Such routes were learnt from R4 and areflagged as external EIGRP routes.
Question:
What is the meaning of an EIGRP External Route?
Question:
How are EIGRP external routes identified?
Question:
What is Two-Way Redistribution?