Memory
The memory unit is used for the storage of binary coded information. Information consists of instructions and data where:
• Instructions are the coded pieces of information that direct the activities of the CPU.
• Data is the information that is processed by the CPU.
The memory hardware contains a large number of cells or locations. Each location may store a single binary digit or a group of binary digits. The cells are grouped so that a complete binary word is always accessed. Word length varies typically from 4-bits up to 64-bits depending upon machine size. Each location in the memory is identified by a unique address, which then allows access to the word. Consequently, to obtain information from the memory, the correct address must be placed onto the address bus.
There are fundamentally two types of memory - primary memory and secondary memory. Primary memory is essential; no computer can operate without this. Secondary memory is necessary to supplement, or back, the primary memory on large computing systems; hence, it is often called backing memory.
There are two types of semi-conductor primary memory: ROM (Read Only Memory) and RAM (Random Access memory). Both types employ solid state circuitry, and are packaged in IC form.
Figure shows how these primary memories are connected to a simple computer bus.
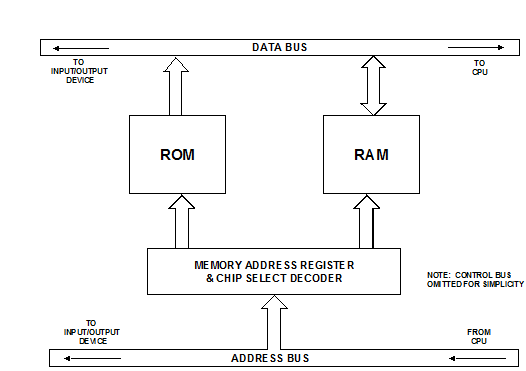
ROM and RAM Connection to Buses