An ATM network is created from interconnected ATM switches. The attachment ports or points can be connected to computers or other ATM switches. As cells reach at an ATM switch, their VPI/VCI is changed using a forwarding table that produced the new VPI/VCI for the next leg of the cell's trip.
The forwarding table is necessarily indexed by the incoming cell's VPI/VCI and the message yield the new VPI/VCI.
LABEL REWRITING:
The placement of the incoming cell's VPI/VCI with a probably distinct VPI/VCI is called rewriting.
ATM is thus known a label switching or label rewriting system. Thus two devices with a connection through an ATM network will likely have distinct VPI/VCI numbers for every end of the connection as given in the figure below.
EXAMPLE:
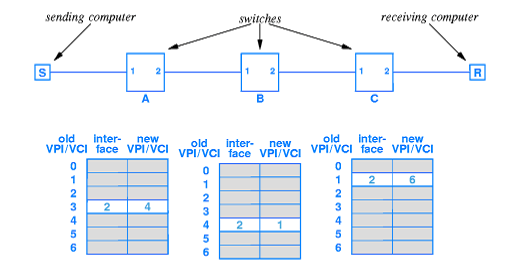
As an example, in the diagram we see that the sending computer S needs a VPI/VCI of 3 and transmits a cell.
Switch A accepts the cell and looks up 3, then rewrites the VPI/VCI as 4, and transmits the cell out of its port 2.
Switch B accepts the cell and looks up 4 then rewrites the VPI/VCI as 1 and transmits the cell at its port 2.
Switch C accepts the cell and looks up 1 then rewrites the VPI/VCI as 6 and transmits the cell out of its port 2.
The receiver computer R accepts the cell with a VPI/VCI of 6, which is the number it is using for the connection. Forwarding tables in every switch must be coordinated to describe meaningful 'paths' through the network.