How does the POP functions? What are the advantages/benefits of IMAP over POP?
POP stands for Post Office Protocol, version 3 (POP3) is one of the easiest message access protocol available which needs installation of POP3 software on the client machine as well as server machine both.
The below drawn figure shows the architectural view of thecommunication which takes place between a POP3 client and a POP3 mail server.
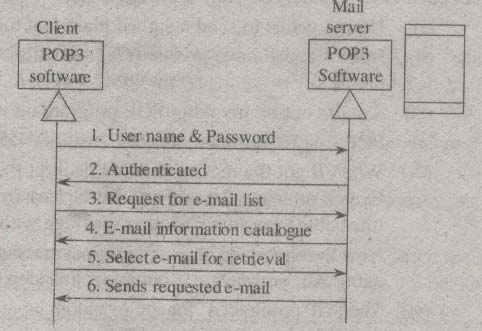
Figure PUP3 Communication
In POP3 communication, the client is required to bring out the e-mails from the mailbox which resides on the mail server. At first, client sends username and password for authorization. The mail server checks the username and password and then provides privileges and permissions o that particular client. The client requests a list of e-mails to which the mail server gives the e- mail information catalogue (including e-mail numbers, sizes and many more). Finally, client retrieves e-mail from mailbox based on the requirement.
POP3 comprises of two message access modes such as keep the mode and delete mode. In the keep mode context, the mail remains in the mailbox once it is retrieved for future reviewing. This mode is generally used when user is remotely accessing mails.
In delete the mode context, the mail gets deleted from mailbox as soon as it is retrieved. This mode is generally used when user is accessing mails from its personal computer( pc), where it can store the mails for future use.
The Internet Mail Access Protocol version 4 (IMAP4) gives certain advantages to the user over the POP3 which are stated below,
(i) E-mail header can be seen before retrieval.
(ii) E-mail contents can be identified with the given string of characters before the retrieval.
(iii) E-mail can be partially retrieved when the bandwidth is quite low and the multimedia contained in e-mail requires high bandwidth.
(iv) A user can have the accessing privileges such as deleting, creating and renaming the mailboxes on mail server.
(v) A collection of the mailboxes can be created in the folder for storing the e-mails.