Q. How can we write an Interrupt Servicing Routine?
The following are the fundamentalthough rigid sequence of steps:
1. Save the system context (flags,registers etc. which will be modified by the ISR).
2. Disable the interrupts which may cause interference if allowed to take place during this ISR's processing
3. Enable those interrupts which may still be allowed to occur during this ISR processing.
4. Determine cause of the interrupt.
5. Take the suitable action for the interrupt like - receive and store data from serial port, set a flag to specify the completion of the disk sector transfer etc.
6. Restore the system context.
7. Re-enable any interrupt levels which were blocked during this ISR execution.
8. Resume execution of the process which was interrupted on occurrence of the interrupt.
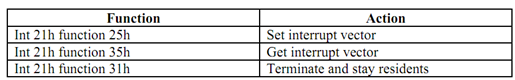
MS-DOS offers you facilities which enable you to install well-behaved interrupt handlers such that they won't interfere with the operating system function or other interrupt handlers. These functions are: