General Considerations for Search
If we may specify the starting state, the operators and the goal check for a search problem, then we know from where to start, how to move and when to discontinue in our search. This leaves the essential question of how to decide which operator to apply to which state at any particular stage in the duration of search. We call an answer to this question a search strategy. Before we concern about exactly what strategy to use, the following need to be taken into consideration:
Path or Artefact
Broadly speaking, there are two different reasons to undertake a search: to find an artefact (a particular state), or to search a way from given state to another given state. Whether you are finding for a way or an artefact will affect several aspects of search of your agent, by including its goal test, what it records along the way and the search scheme available to you.
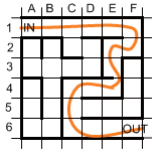
For example, in the jumble below, the game involves finding a route from the top left hand corner to the bottom right hand corner. We know what the exit looks like (a gap in the outer wall), so we do not find for an artefact. Rather then, the point of the search is to find a path, so the agent might remember where it has been.
However, in another search, the point of the search is to find something, and it may be immaterial how you searched it.