Describe the functions and significances of all fields (such as Source Port and Destination Port) of a TCP header.
Functions and significance of tcp header's fields
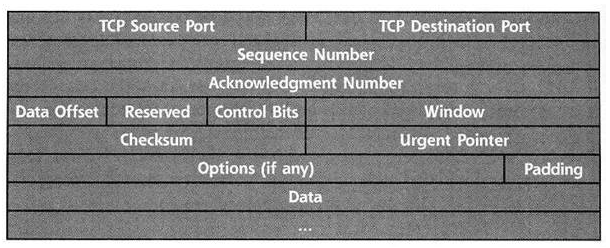
FIELDS
TCP Source Port
The TCP Source port has the port number; from this port packets are sent. This port is dynamically assigned by the stack of TCP.
TCP Destination Port
The TCP Destination port has a port number and from this port number packets are routed.TCP stack is responsible for routing data to destination point.
Sequence Number
The sequence number is used for initializing the session in TCP.
Acknowledgment Number
The Acknowledgement Number is number assigned for session initialization.
Data Offset
The Data offset is meant for ending the header of TCP packet and from that point data starts and that data ends is equal to the 32 bit words.
Reserved
This field is responsible for handling future requirements.
Control Bits

URG (Urgent)
The Urgent pointer in the TCP Header field is of great significance. The urgent pointer points to the data of the packet where urgent data has been saved.
ACK(Acknowledge)
The Acknowledgement is a bit which have a lot of importance. The acknowledgement is used to acknowledge the earlier sent packets.
Push Function
The push function is used to destroy data through the TCP layer.
Reset
In Reset connection is again reset if there had been any error or any kind of interruption.
Synchronize
In this, system generates some synchronized sequence number and assigns it to sessions and this sequence number is used during the establishment of session.
Finish
If there is no data there to send from the sender then the session will be finished.
The length of TCP header is of 32 bit
Window
The window is meant for providing a way of each side of communication that provides a way of checking the flow of packets to the destination point and also be sure that all packets have been received properly by the receiver before sending any new packet to the receiver.Checksum
The Checksum provides a way for checking and verifying that TCP packet that includes header and data should not corrupt in its journey across the network.
Urgent Pointer
This field has a Pointer into the data of the packet to indicate where urgent information is located.
OPTIONS
The options include the additional information about the TCP processing capabilities used during connection between Source and Destination.
Padding
The padding is used to extend the length of the TCP Header its initial bit set to 0.It makes sure that every packet should be send properly.
Data fields
Data fields are used for urgent data.