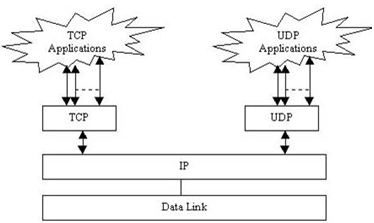
Q. Function of TCP/IP Transport Layer ?
TCP/IP Transport Layer
- Defines two standard transport protocols UDP and TCP
- TCP equipment a dependable data-stream protocol
- UDP implements an undependable data-stream
- TCP offers reliable data transmission
- UDP is helpful in many applications
- e.g. Where data requirements to be broadcasted or multicasted
- Primary difference is that UDP doesn't necessarily provide reliable data transmission
- Several programs will use a separate TCP connection as well as a UDP connection
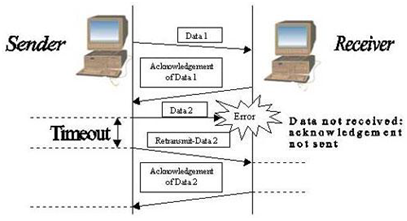
- TCP is accountable for data recovery
- By providing a series number with each packet that it sends
- TCP needs acknowledgement (ACK) to ensure correct data is received
- Packet is able to be retransmitted if error detected
- Use of acknowledgement (ACK)
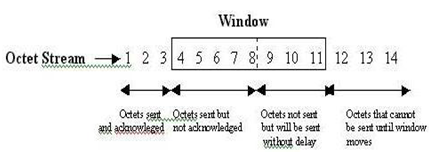
- Flow control with Window
- by means of specifying an acceptable range of sequence numbers
- UDP and TCP introduce the concept of ports
- Common ports as well as the services that run on them:
FTP 21 and 20
telnet 23
SMTP 25
http 80
POP3 110
- By specifying ports as well as including port numbers with TCP/UDP data multiplexing is achieved
- Multiplexing permits multiple network connections to take place simultaneously
- The port numbers together with the source and destination addresses for the data determine a socket