What do you understand by cryptanalysis? Discuss about the transposition ciphers substitution cipher, and onetime pads.
The messages which are intended to transmit secretly and securely with full protection are subjected to the process of encryption and decryption in order to provide the desired security. The original message which is to be encrypted is called plain text. This plain text is transformed by a function with the encryption key (K) as parameter. The plain text after the transformation that is the output of the encryption process is called as cipher text. And this cipher text or the encrypted message with key is actually transmitted.
Although an intruder listens to this message/cipher text by catching the communication channel still he cannot decrypt the cipher text because he doesn't know key. Even though he doesn't know the key still he is able to break that cipher text at times and that art of breaking ciphers is known as cryptanalysis.
The art of devising and breaking ciphers is collectively called as cryptology. The encryption methods/techniques are, divided into the following two categories,
1. Substitution Ciphers
2. Transposition Ciphers.
1. Substitution Ciphers:
In this cipher, each letter or the group of letters is replaced by another group of letters. Good instance of substitution cipher is Caesar cipher. In this cipher, a becomes D, and b becomes E and so on and the Z becomes C.
An Example is written below:
An Attack becomes DWWDFN
This general system is called the mono alphabetic substitution.
In substitution ciphers, order of letters is similar to that of plain text but just disguises them.
2. Transposition Ciphers
In contrast to the substitution ciphers, transposition ciphers read the letters but do not disguise them. The key of this cipher is a word, having no repeated letters. An instance of a transposition cipher text is given below.
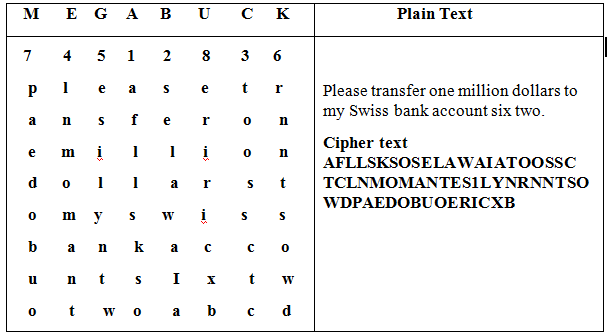
The main purpose of the key is to number the columns. The plain text is in rows and cipher text is prepared by assembly letters in columns.
Onetime Pads is defined below:
There is a simple way of constructing an unbreakable cipher. The procedure is initiated with the choice of a random bit string as key. Converting plaintext into a bit string and computhexc1usjve OR operation for these two strings This method/technique is known as Onetime Pad.