Explain the differences between Logical and physical address space
Logical Vs physical address space
(1) An address produced by the CPU is commonly referred to like a logical a logical address. The set of all logical addresses generated through a program is termed as logical address space. While, an address seen by the memory unit- which is, the one loaded in the memory-address register of the memory- is usually referred to as physical address. The set of all physical addresses consequent to the logical addresses is termed as physical address space.
(2) The methods of compile-time and load-time address-binding produce identical logical and physical addresses. Nevertheless, in the execution-time address-binding scheme and the logical and physical-address spaces are differing.
(3) The user program never considers the physical addresses. The program create a pointer to a logical address, as 346, stores this in memory, manipulate this, compares this to other logical addresses- all as the number 346.
Only while a logical address is used as memory address, this is relocated relative to the relocation or base register. The memory-mapping hardware device termed as the memory- management unit (MMU) converts logical addresses in physical addresses.
(4) Logical addresses range from 0 to max. User program which generates logical address thinks which the process runs in locations 0 to max.
Logical addresses must be mapped into physical addresses before they are utilized.
Physical addresses range from (R+0) to (R + max) for a relocation register or base value R.
(5) Example:
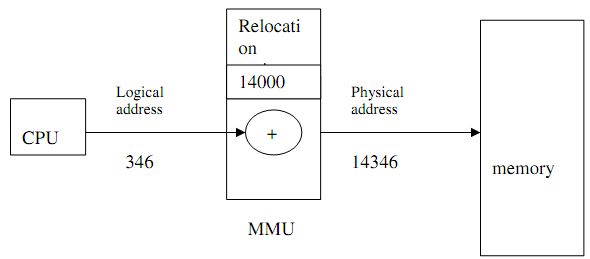
Mapping from logical to physical addresses by using memory management unit (MMU) and relocation or base register
The value into relocation/base register is added to all logical address generated through a user process, at the time this is sent to memory, to produce corresponding physical address.
In the above diagram, base/ relocation value is 14000 then an attempt through the user to access the location 346 should map to 14346.