Explain process scheduling in time sharing
The relevant features of time sharing are:
1. Process priorities do not depend on the nature of the processes
2. Processes are scheduled in the Round Robin manner
3. A running process is pre-empt when its time slice elapses
4. Processes perhaps swapped out of memory
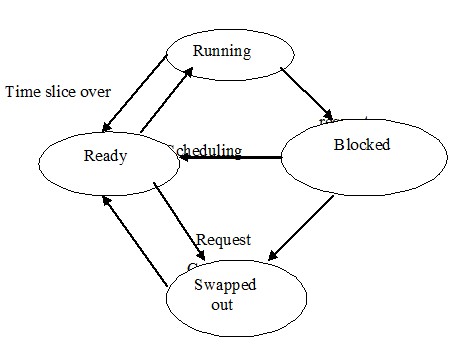
A repercussion of the round robin scheduling is that the priority of a process changes dynamically during its life time. It is the uppermost priority process when it is scheduled. It becomes the lowest priority process while it finishes its time slice or when it is blocked because of an IO request. Its efficient priority increases with time as it waits for the CPU
The action of the time sharing scheduler perhaps summarized as follows:
1. The scheduler maintains 2 different PCB lists- one for ready processes and another for blocked and swapped out processes
2. The PCB list for ready processes is prepared as a queue
3. The PCB of a newly created process is able to be added to the end of the ready queue
4. The PCB of a terminating process is able to be simply removed from the system
5. The scheduler always selects the PCB on the head of the ready queue
6. When a running process complete its time slice or makes an IO request its PCB is removed from the ready queue to the blocked/swapped-out list
7. When the IO operation anticipated by a process finishes its PCB is moved from the blocked/swapped out list to the end of the ready queue