With a neat diagram explain operation of time multiplexed space switching.
Time division switches, an inlet or an outlet corresponded to a particular subscriber line with one speech sample appearing each 125 µs on the line. These switches are used in local exchanges. We here consider switches which are needed in transit exchanges. Now, the inlets and outlets are trunks that carry time division multiplexed data streams. We call such switches time multiplexed switches. A time multiplexed time division space switch is demonstrated in figure. There are N incoming trunks and N outgoing trunks, all carrying a time division multiplexed stream of M samples per frame. All frames are of 125-µs time duration. In individual frame time, a total of MN speech samples have to be switched. Individual sample duration, 125/M microseconds, is typically referred to as a time slot. N-samples are switched, in one time slot. Figure demonstrates an output-controlled switch. The output of this is cyclically scanned. There is a 1-to-M relationship among the outlets and the control memory locations that is there are M locations in the control memory consequent to each outlet.
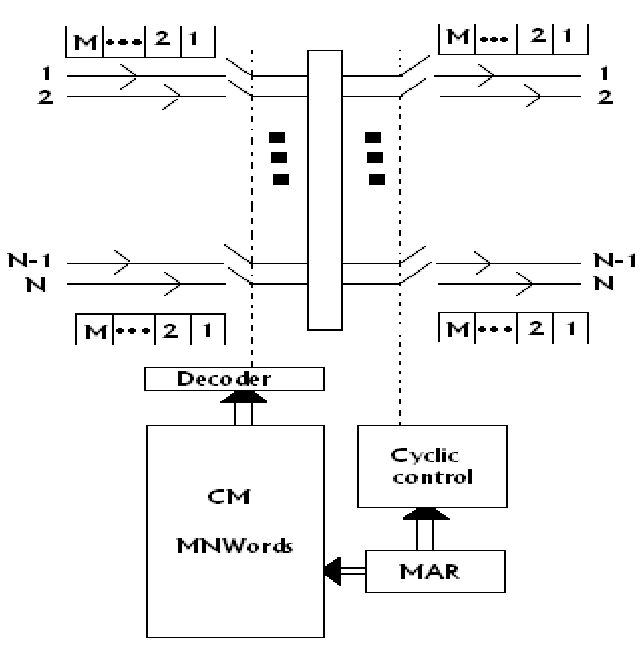
FIG - Time Multiplexing Space Switch
The control memory has MN words. When we view the control memory like M blocks of N words each, a location address may be given in a two dimensional form,(i,j),here i is the block address and j is the word inside the block. We have 1< i < M and 1< j < N. The block addresses i match to the time slot i and the word address j to the outlet j. The first N locations of the control memory correspond to the first time slot, the subsequent N locations, that is locations N + 1 to 2N while addressed linearly, or locations (2,1) to (2,N) while addressed in a two dimensional form, correspond to the time slot 2etc. Thus, if the location (i,j) hold an inlet address k, this implies that inlet k is related to the outlet j in the time slot i. The number of trunks which can be supported on this switch is specified by N =125/ Mt, here t is the switching time containing memory access time per inlet-outlet pair.