Q. Explain Open-systems interconnections architecture model
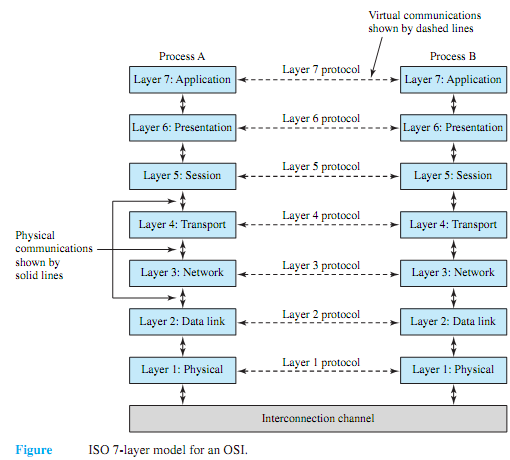
The most common network architecture model is the open-systems interconnections (OSI). Figure shows the ISO (International Standards Organization) seven-layer model for an OSI. Although not all layers need be implemented, the more layers that are used, the more functionality and reliability are built into the system. Starting from the bottom layer, the functions of the layers are as follows.
1. Physical-Defines the type of medium, the transmission method, and the transmission rates available for the network; provides the means for transferring data across the interconnection channel and controlling its use.
2. Data Link-Defines how the network medium is accessed, which protocols are used, the packeting/framing methods, and the virtual circuit/connection services; responsible for the transfer of data across the link; provides for the detection and correction of data- transmission errors.
3. Network-Standardizes the way in which addressing is accomplished between linked networks; performs networking functions and internetworking.
4. Transport-Handles the task of reliable message delivery and flow control between applications on different stations; provides source-to-destination data integrity.
5. Session-Establishes two-way communication between applications running on different stations on the network; provides the user interface into the transport layer.
6. Presentation-Translates data formats so that computers with different "languages" can communicate; provides the syntax (rules) of representation of data between devices.
7. Application-Interfaces directly with the application programs running on the stations; provides services such as file access and transfer, peer-to-peer communication among applications, and resource sharing; provides support to process end users' applications such as electronic mail, database management, and file management.