Explain in DES Data Encryption Standard :DES stands for Data Encryption Standard and is explained as follows:
DES is at present the most widely used key cryptographic systems. DES can be implemented much efficiently in hardware rather than in software.
In this method/technique, DES first splits the original message into blocks of 64 bits. Each block of 6 bit plaintext is separately encrypted into the block of 64 bit cipher. DES makes use of a 56 bit secret key. There are nearly 19 stages in this algorithm out of which 16 stages are for the iteration of the message. This is shown in figure drawn below. The encryption process is reverse of the decryption. Every step in DES takes 64 bit input from preceding step and produces a 64 bit output for the next step.
The first step performs the initial transformation/permutation of 64 bit plaintext. The last step performs the transformation just in the reverse of the initial transformation.
The stage earlier than the last stage performs the 32 bits swap of the message encrypted in the 16 iterations. The working it is shown in the figure drawn below.
Each iteration splits the 64 bit text into 32 bit inputs and produces the two 32 bit outputs. The left output is straight a copy of the right input. The right output is the bitwise of the EXCLUSIVE OR of the left input and the function of right input and key for this phase Ki.
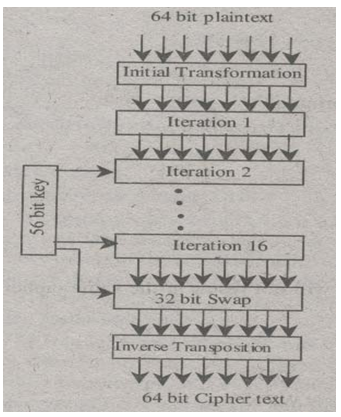
Figure General Outline of DES
Figure Working of One Iteration
Before an algorithm begins, a 56 bit transposition is applied to the key. The key is divided into two 28 bit units before iteration. These 28 bit units are rotated left by the number of bits depending upon the iteration number. Ki is derived from this rotated key by applying another 56 bit transposition to it. A different 48 bit subset of 56 bit is extracted and permuted on each round of it.
DES Chaining is described below:
The DES works in the Electronic code book mode, this mode might give a chance to break the DES, if the structure of message is recognized by the intruder. This can be closed by chaining all the block ciphers. One way of chaining is known as “Cipher block chaining”.
In this method/technique, each plaintext block is EXCLUSIVE OR ed with the previous cipher text block before applying encryption. The first block is EXCLUSIVE OR ed with the randomly chosen Initialization Vector (IV) which is transmitted along the cipher text. The chaining of blocks is shown in figure drawn below EXCLUSIVE OR is denoted by #.
Encryption is explained below:
The ciphertext of first block can be computed by using the, C0=E(P0 XOR IV) The ciphertext of the blocks remaining can be computed by using this formula,
C = E (Pi XOR Ci-1)
Decryption is discussed below:
The plaintext of text block in the decryption can be computed by the following formula
P0=IV XOR D(C0)
The plaintext of other blocks can be computed by using the following formula
P1= P0 XOR D(C1)
Cipher block chaining has the benefit that the same plaintext block will not result in the same ciphertext block.