Explain CPU based exchange.
CPU Based Exchange: All the control equipment is replaced with a single processor that must be quite powerful, in centralized control. This should be able of processing 10 to 100 calls per second, depending upon the load on the system, and performing simultaneously of many other ancillary tasks. A usual control configuration of an ESS by using centralized SPC is demonstrated in figure. A centralized SPC configuration may utilize more than one processor for redundancy reasons. Though, there are a large number of services that can be offered by CPU based exchange, they might be grouped under four wide categories.
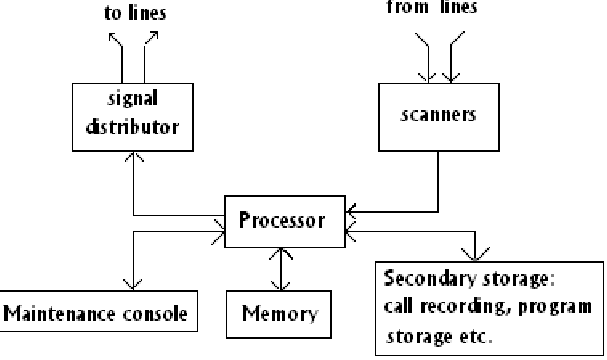
FIG - Typically CPU Based Exchange
1. Services related with the calling subscribers and designed to decrease the number of dialing errors and the time spent on dialing.
2. Services related with the called subscriber and designed to raise the call completion rate.
3. Services including more than two parties.
4. Various types of services.
These new services are termed as supplementary services and several of the prominent ones are given below as:
Category 1:
- Recorded number calls or no dialing calls
- Abbreviated dialing
- Call back while free.
Category 2:
- Operator answer.
- Call forwarding
Category 3:
- Call waiting
- Calling number record
- Conference calls.
- Consultation hold
Category 4:
- STD barring
- Automatic alarm
- Malicious call tracing
Issues commands of a subscriber to an exchange to deactivate or activate a service, record or solicit an acknowledgement or clear data in the subscriber line data area from the exchange. As an illustration, a user may enable or disable STD service on his line by using a command. A command may be or not have data related with this. The number of digits in the data, while present, may vary depending on the command. As an effect, subscriber commands are designed to be of variable length requiring the use of an end-of-command symbol.