Explain 100 line exchange with two-motion line finders.
Design: In such design, here are 24 line finders. When any of the 100 subscribers has to find access to any of the 24 two-motion selectors, this is necessary that every line finder is able of reaching any of the 100 subscribers. Conversely, each line finder should have 100 outlets. For this purpose, two motion selectors have to be used as line finders. The configuration is demonstrated in figure. The corresponding outlets of the line finders are commoned. Likewise, the outlets of the numerical selectors are commoned also.
While the start condition is received, line finder is caused to hunt vertically till the wipers reach a marked level. The vertical hunting is after that stopped and the horizontal hunt commences to get a particular marked contact in this level. This may be noted that into the extreme case, the line finder need take 20-steps -10 vertical and 10 horizontal -before a line is determined. The line finders are made to step automatically, by using interrupter contact mechanism. If the line finder locates the subscriber line, start condition is removed, the allotter switch steps on to the subsequent free line finder in readiness for additional calls, and the numerical selector sends out the dial tone to the subscriber in readiness to get dialing pulses. After that the establishment of the connection proceeds in the usual way.
Evidently, Design 3 is by far the best for a 100-line exchange. When we had used uni selectors as line finders, this would have been essential to divide subscriber's line in small groups of, as 24 each. These designs involving groupings, function efficiently only in certain specific traffic conditions and usually lead to higher blocking probabilities.
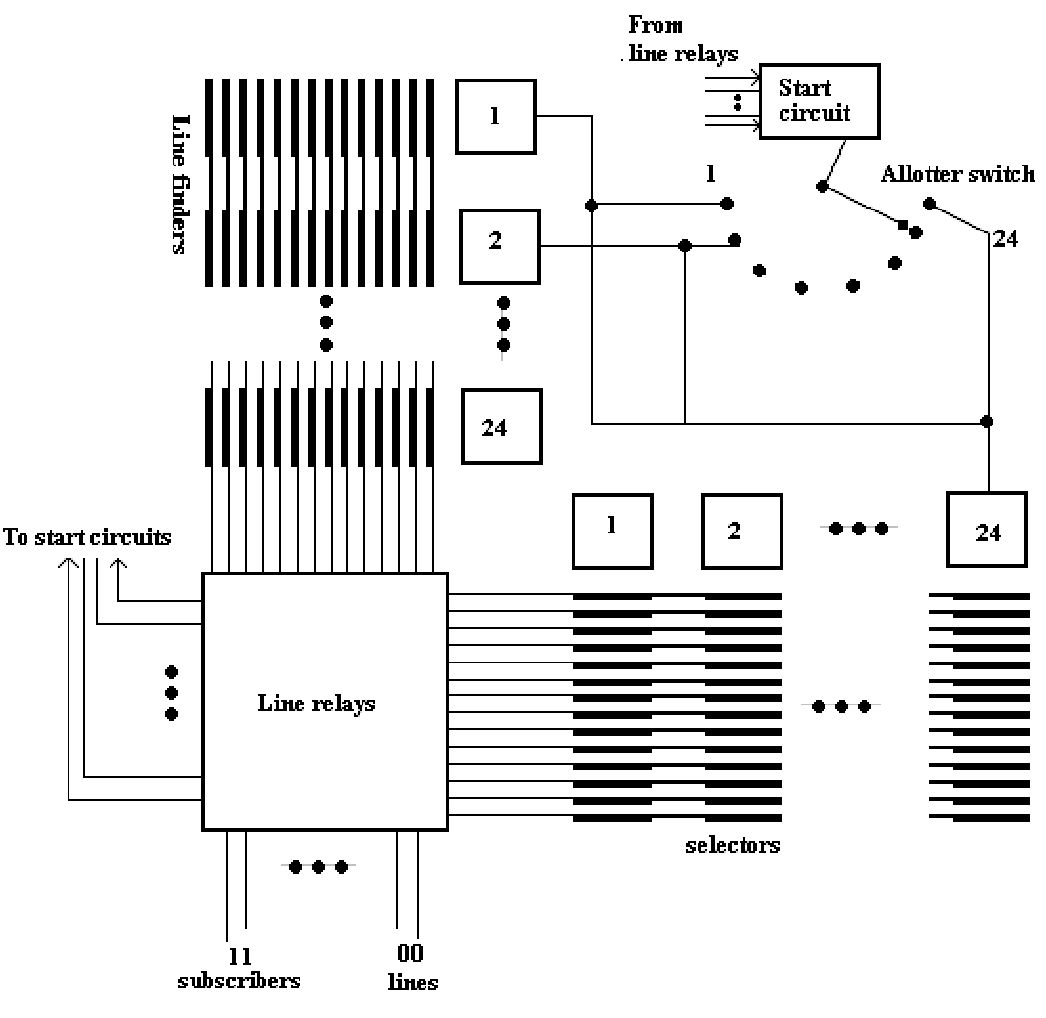
FIG - 100-Line exchange with two-motion line finders