Q. Example on Cyclic Distribution of data?
!HPF$ PROCESSORS P1(4)
!HPF$ TEMPLATE T1(18)
!HPF$ DISTRIBUTE T1(CYCLIC) ONTO P1
The result of these instructions is displayed in Figure below.
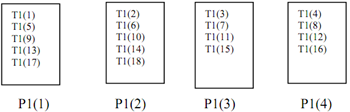
Figure: Cyclic Distribution
However in an analogous alternative of cyclic distribution
!HPF$ DISTRIBUTE T1 (BLOCK (3)) ONTO P1
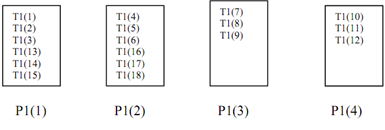
Figure: Variation of Cyclic Distribution
It covers case where both template and processor are one dimensional. When the and processor have (same) higher dimension every dimension is able to be distributed separately mixing any of four distribution formats. The correspondence between template and processor dimension is the obvious one. In! HPF$ PROCESSORS P2 (4, 3)
!HPF$ TEMPLATE T2 (17, 20)
!HPF$ DISTRIBUTE T2 (CYCLIC, BLOCK) ONTO P2
The first dimension of T2 is distributed cyclically over first dimension of P2 the second dimension is distributed block wise over second dimension of P2.
(c) * Distribution
Some dimensions of a template can have 'collapsed distributions' allowing a template to be distributed on a processor arrangement with fewer dimensions than the template.