The objective of this example is to demonstrate the steps required for a successful attack against a vulnerable Windows XP SP2 system. It will show: a) how Nessus can be used to discover vulnerabilities in a system,
b) how a vulnerability can be exploited using Metasploit, c) the Meterpreter functionality d) a password
cracking example, e) the Netcat functionality, f) how an attacker can gain GUI access into a remote system. In the discussion below Bt4 and WinXP refer to virtual machines Backtrack4-Final and Windows XP SP2, respectively; although Bt4 is used here, similar steps will be used in the case of Bt5. Note that red color is used for the commands. In this example, I discuss the steps that I followed. It is strongly recommended that you use your own virtual machines and follow the same steps as you go over this example; in this case you have to replace my settings such as last name, IP address, etc. with your settings.
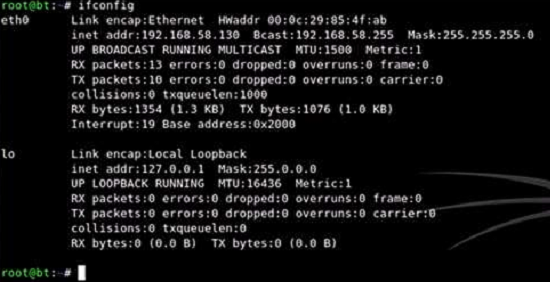
As you can see above, my Bt4 has address 192.168.58.130; your Bt4 will have a different IP address. Note that WinXP should be on the same subnet with Bt4. This means that, in my case, the leftmost three bytes of the WinXP address must be "192.168.58". Thus, I can find its IP address by using an Nmap SYN scan. Before I proceed, I disconnected from the Internet and disabled all firewalls, antivirus software, and access controls that were running on my laptop. I did that because these tools will interfere with the Bt4, WinXP interaction and prevent me from analyzing correctly as well as exploiting the vulnerabilities of WinXP. After I had finished with this exercise, I re-enabled all these security tools before I connected back to the Internet.