Q. Environment of the Packet Flow?
Protocol stack used on Internet is referred to as TCP/IP protocol stack. If we were to follow the path that message "Hello computer 5.6.7.8!" took from our computer to computer with IP address 5.6.7.8, it would take place something like this:
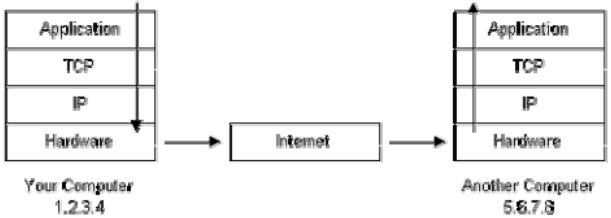
Figure: Environment of the Packet Flow
1. Message would start at the top of protocol stack on your computer and work its way downward.
2. If the message to be sent is long, every stack layer that message passes through may break the message up into smaller chunks of data. This is since data sent over the Internet (and most computer networks) are sent in manageable chunks. On the Internet, these chunks of data are known as packets.
3. Packets would go through Application Layer and continue to the TCP layer. Every packet is assigned a port number, which is used by program on destination computer to receive message since it will be listening on a specific port.
4. After going through TCP layer, packets proceed to IP layer. This is where every packet receives its destination address, 5.6.7.8.
5. Now that our message packets have a port number and an IP address, they are ready to be sent over Internet. Hardware layer takes care of turning our packets containing alphabetic text of our message in electronic signals and transmitting them over the phone line.
6. On the other end of phone line your ISP has a direct connection to Internet. ISPs router examines destination address in every packet and determines where to send it. Generally, the packet's next stop is another router.
7. Ultimately, packets reach computer 5.6.7.8. Here, packets start at the bottom of destination computer's TCP/IP stack and work upwards.
8. As packets go upwards through the stack, all routing data that sending computer's stack added (like port number and IP address) is stripped from packets.
9. When data reaches top of the stack, packets have been re-assembled into their original form, "Hello computer 5.6.7.8!"