Minimize the logic function Y(A, B, C, D) = ∑m(0,1,2,3,5,7,8,9,11,14). Use Karnaugh map.
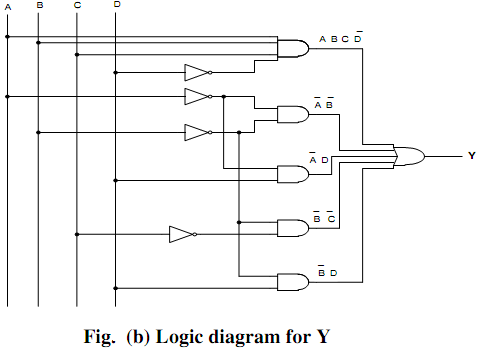
Draw logic circuit for the simplified function.
Ans: In following figure (a) shows the Karnaugh map. Because the expression has 4 variables, the map has sixteen cells. The digit one has been written into the cells containing a term in the provided expression. The decimal number has been added like subscript to specify the binary number for the concerned cell. The term ABC D can't be merged along with any other cell. Therefore this term will show as such in the last expression. Here four groupings of 4 cell each. All correspond to the min terms (0, 1, 2, 3), (0, 1, 8, 9), (1, 3,5,7) and also (1, 3, 9, 11). All are represented in the map. Because all the terms (except 14) have been combined in groups of 4 cells, there is no requiring forming groups of two cells.
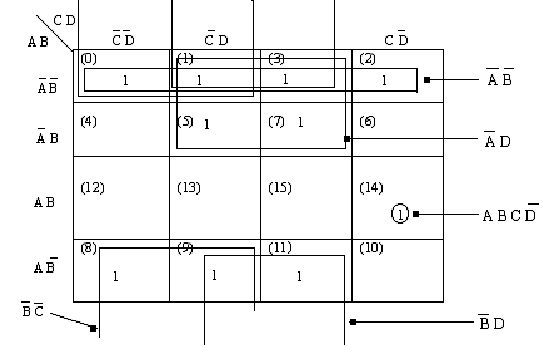
Figure (a)
Hence simplified expression is Y (A,B,C,D) = ABC D + A B + B C + B D+ A D Fig.4 (b) shows the logic diagram for the simplified expression
Y (A,B, C, D) = ABCD‾+ A‾B‾+ B‾C‾+ B‾D‾+ A‾D