Systems Life Cycle Approach
Systems Analysis and Design follows a life cycle for development, as shown below. Brief discussion on this approach is given here:
Figure : Systems Life Cycle Approach
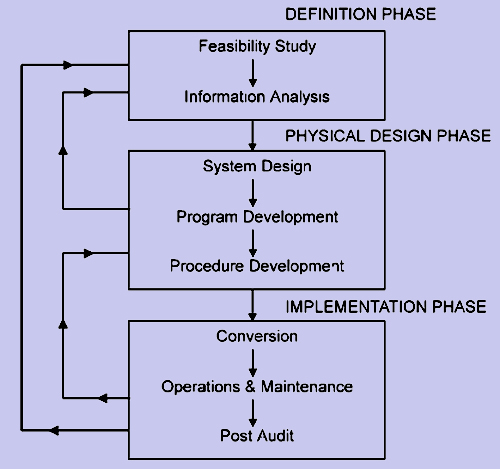
DEFINITION PHASE
In this phase firstly, a feasibility study is conducted to check the viability of the project. This consists of checking of Economic feasibility, Technical feasibility and the Operational feasibility. Once a decision is taken to initiate the project with predefined objectives, then a thorough study of the existing system is made. This involves studying and documenting formal as well as informal flow of information. The documentation is done using standard systems analysis tools like System Flow Chart, Grid Chart, Decision Tables, Data Flow Diagrams, Warnier Diagrams, etc. Besides these, the Systems Analyst has to identify the information needs of various managers. This is generally done using personal interviews.
The comparison between the existing system and managerial requirements will provide deficiencies, weaknesses of the system, if any. Based on this, a conceptual design of the proposed system is generally arrived at, which is submitted to user managers and a feedback is taken.
PHYSICAL DESIGN
The conceptual design accepted by user managers is the starting point of this phase. Here, a detailed design is created with I/O design, data base designs and processing module design. Coding in high-level language is done. At this stage, detailed control procedures, security guidelines and back up procedures are laid down in detail.
The documentation of the designed system is extremely important. The following manuals must be created:
- User Manual
- Systems Manual
After the completion of this phase, the system is ready to be implemented in practice.
IMPLEMENTATION
During this phase, actual changeover from the old system to the new system takes place. Either, the two systems are run in parallel for sometime and then the old system is dropped after the new one stabilizes. Alternatively, at a fixed instant the old system is dropped and the new system implemented. Generally, in Indian context, parallel conversion is considered to be the safer one.
Irrespective of the quality of the system implemented, there will always be continual changes in user requirements and also some error might crop up during processing. There is a need for on-going maintenance of the system. It has been found that over the total life cycle of a software package, more than 50% of budget is spent on maintenance.
The last item of system life cycle is Post Audit. In this module, efforts are made to compare the planned versus actuals from the view of gaining valuable insight in software development. All aspects of the system are reviewed and documented. As can be seen from the figure, there are feedback loops from one phase to another. The whole process is repeated till user satisfaction is achieved.