Combinational/Sequential Logic design with Integrated Circuits (Dual in line package)
Car wash concept with the following steps in a Combinational Logic Diagram:
1. Start Rinse
2. Stop Rinse, Start Soap
3. Start Brush
4. Stop Soap, Stop Brush
5. Start rinse
6. Stop rinse, Start Dry
7. Stop Dry
A corresponding LED will light-up when the step is reached on during the car wash sequence/run. Each LED will be on for 5 seconds. For steps 2, 4, and 6, those LEDs will light for 8 seconds.
Requirements: Design Combinational/sequential electronic logic diagram with integrated Circuit items depicted an automated Car Wash process. All of the integrated circuits used thus far in the course have been 74LS00s and 74000s series.
From the diagram I will actually construct the project on a Pencil Box Logic Designer which has an experimental breadboard. Items used in/on the diagram will include some of the following ICs that can be placed on breadboard:
Logic Gates:
AND gate
Exclusive-OR (XOR) gate
Inverter gate
NAND gate
NOR gate
OR gate
TIMER
Half-Adder
Full-Adder
Comparators
Binary Decoders
Binary-to-Decimal Decoders
Multiplexer (MUX)
Demultiplexer (DEMUX)
Latch
S-R Latch
Gated S-R Latch
D Latch
FLIP-FLOPS
D flip-flop
J-K flip-flop
One shot
Counters & Counter logic operations
Shift Registers
Serial In/Serial Out
Serial In/Parallel Out
Note: Some of the items on the list are combinations of several ICs. Example: Instead of using XOR gate for logic functions on the diagrams, it can also be a combination of 2 x Inverter Gates, 2 x AND Gates, & 1 x OR Gate.
The PencilBox Logic Designer which I'm using has Logic Indicators (8 x LED), CLOCK, Logic 8 x Switches, 2 x PULSERS push buttons.
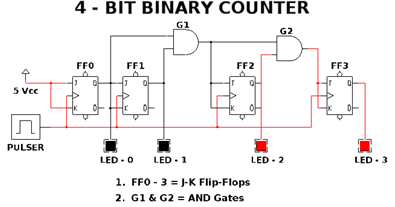
The last diagram I completed was a 4-Bit Counter. See below: