(a) Suppose that t is a binary tree of integers (that is, an object of type BinTree of Int.) in the state shown in Figure 3.
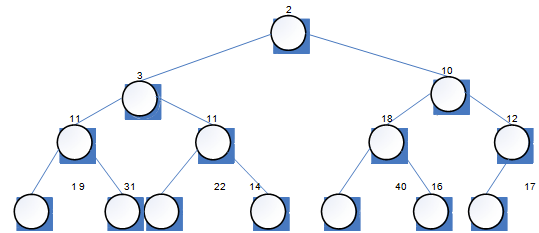
Give the vectors returned by each of the following expressions.
(i) LEVEL_ORDER(t)
(ii) IN_ORDER(t.leftTree( ))
(b) suppose that v is an object of type VectorPlus of mString in the state ["tawny", "little", "barn", "long-eared", "eagle", "scops"]
In answering this part of the question you may, if you wish, use the WorkPad.
(i) Suppose that the strings in the vector v are rearranged into a sorted vector (where the strings in v arc compared using the lexicographic order described on page 32 of Unit 8). G i v e t h e vector that results from this rearrangement
(ii) Suppose that, the function GROW_TREE is applied to the sorted vector which you gave in part (i). Give the binary search tree which is returned by GROW_TREE.
(iii) Suppose that. The string "hawk" is inserted into the binary search tree which you gave in part (ii), using Strategy 3.2 of Unit 8. Give the resulting tree.
(c) The tree in Figure is a heap tree. Use Strategy 3.4 of Unit 8 to remove the root item from that tree. Give the binary tree produced by this strategy.