Q. Describe THEAD, TBODY and TFOOT tag?
THEAD, TBODY, TFOOT
<THEAD>, <TBODY>, and <TFOOT> form groups of rows. <THEAD> specifies that a group of rows are header rows at the top of the table. <TBODY> specifies that a group of rows are body rows. <TFOOT> specifies that a group of rows are footer rows at the bottom of the table.
The most popular use for these three tags, that are currently only recognized by MSIE 4 and up, is to put borders among groups of rows instead of between every two rows. For illustration, suppose you have a table in which you want borders around the top row, bottom row and around the entire block of rows in between. You could do that with following code. Note that in addition to <THEAD>, <TBODY> and <TFOOT> you also should use <TABLE RULES=GROUPS>. The below example illustrates the use of these tags:
<HTML>
<BODY>
<TABLE CELLPADDING=6 RULES=GROUPS FRAME=BOX>
<THEAD>
<TR> <TH>Weekday</TH> <TH>Date</TH> <TH>Manager</TH>
<TH>Qty</TH> </TR>
</THEAD>
<TBODY>
<TR> <TD>Mon</TD> <TD>09/11</TD> <TD>Komal</TD> <TD>639</TD>
</TR>
<TR> <TD>Tue</TD> <TD>09/12</TD> <TD>Lovely</TD> <TD>596</TD>
</TR>
<TR> <TD>Wed</TD> <TD>09/13</TD> <TD>Rohan</TD> <TD>1135</TD>
</TR>
<TR> <TD>Thu</TD> <TD>09/14</TD> <TD>Suresh</TD> <TD>1002</TD>
</TR>
<TR> <TD>Fri</TD> <TD>09/15</TD> <TD>Rohan</TD> <TD>908</TD>
</TR>
<TR> <TD>Sat</TD> <TD>09/16</TD> <TD>Lovely</TD> <TD>371</TD>
</TR>
<TR> <TD>Sun</TD> <TD>09/17</TD> <TD>Suresh</TD> <TD>272</TD>
</TR>
</TBODY>
<TFOOT><TR> <TH ALIGN=LEFT COLSPAN=3>Total</TH> <TH>4923</TH>
</TR></TFOOT>
</TABLE>
</HTML>
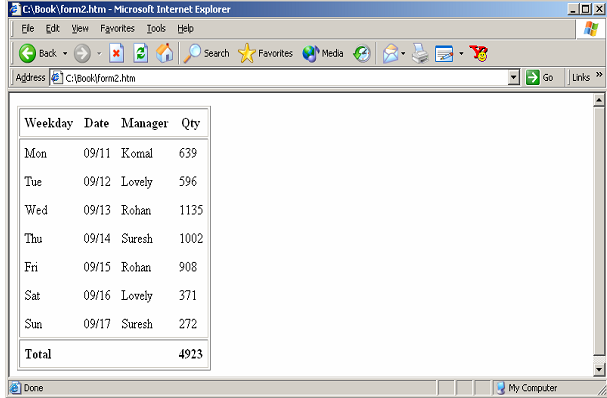
Figure: Using the THEAD, TBODY and TFOOT Tags