Describe the static hash file with buckets and chaining and show how insertion, deletion and modification of a record can be performed.
In static hash file organization, the word bucket is used to associate a unit storage in which can store one or more records. A file consists of buckets 0 through N-1, with one primary page per bucket initially and additional overflow pages chained along with bucket, if needed later.
Buckets holds data entries (or data records). In hashing scheme, a hash function, h, is perform on the key of the record to identify the bucket to that data record belongs to.
The hash function is an significant component of the hashing approach. The major problem along with static hash file is in which the number of buckets is fixed.
Insertion of a record - To insert a data entry, the hash function is used to recognize the
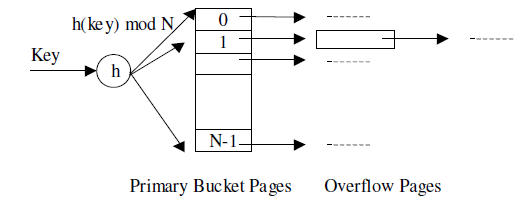
Static Hash File
correct bucket and then put the data entry there. If there is no space for this data entry, a latest overflow page will be allocated, put the data entry on this page or the page to the overflow chain of the bucket.
Deletion of a record - To delete a data entry, the hash function is used to recognize the correct bucket, locate the data entry through searching the bucket, and then erase it. If the data entry is the last in an overflow page, the overflow page is erased from the overflow chain of the bucket and added to a list of free pages.
Modification of a record - To modify a data entry, the hash function is used to recognize the correct bucket, locate the data entry through searching the bucket and contain it, modify the data entry, and then rewrite the modified data entry on it.