CONCEPT OF PACKET :
Network systems splits data in small junks or blocks known as packets, which they send individually. Why we required packets rather than bits? The answer to this problem is because a receiver and sender need to coordinate to detect transmission exceptions. Also the individual connection between every pair of computers is not exist. That's why to solve these problems shared network connections are created among many workstations.
PROBLEMS WITH SHARING:
The demand of sharing is increasing very rapidly because many computers machine have to use the shared networks. In addition to this some programs have large data transfer. In this process they access the network for long time. But on the other way some programs cannot wait so long. So we require a method for fairness.
SOLUTION FOR FAIRNESS:
To the fairness, the solution is to split the data into small chunks or block called 'PACKETS'. Computers take turns to transmit one packet at a time over the shared connection. Because every packet is small so no computer experiences a long delay.

In the diagram one reason for using the packets is explained. We see that in a shared resource when one pair of computer interacts, the other have to wait. To understand the need of packet here, let's see a transmission with data packets in the diagram.
WITHOUT PACKETS:
A 5MB file transmitted across network with 56Kpbs capacity will need 12 minutes. This seems that all that computers will have to wait for 12 minutes before starting other transfers.
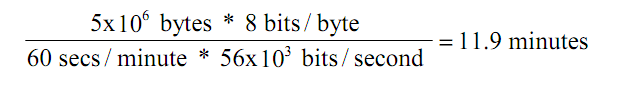
WITH PACKETS:
Now if the file is divided into packets, other computers must only wait until packet has been transmit.
Suppose file is divided into 1000 byte message. Now every data packet takes less than 0.2 seconds to send it. Here other computers have only
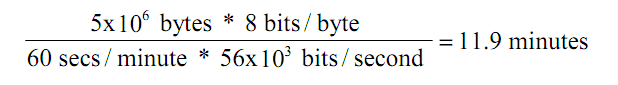
wait for 0.14 sec before starting to transmit.