Q. Define Checkbox in html?
Checkboxes are used when one or more out of the group of options is to be chosen. Building Check boxes is very similar to radio buttons. Figure explains the use of Checkbox.
User can choose any number like 1, 2, none or all of the options. Choices would be returned to you as the name/value pairs
Tom=YES
Terry=YES
(Or whatever the user chooses. If nothing, nothing would be returned to you)
Following is the code for making a table which contains different options for 3 different questions. Try it yourself and see the result.
<CENTER>
<TABLE WIDTH=600 BORDER=1 CELLSPACING=1><TR>
<TD WIDTH=199>
Which of these guys are your friends?<BR>
<INPUT TYPE=CHECKBOX NAME="Friend?..Tom" VALUE="YES"> Tom
<BR>
<INPUT TYPE=CHECKBOX NAME="Friend?..Ricky" VALUE="YES"> Ricky
<BR>
<INPUT TYPE=CHECKBOX NAME="Friend?..Terry" VALUE="YES">
Terry<BR>
<INPUT TYPE=CHECKBOX NAME="Friend?..BU" VALUE="YES"> Bunty<P>
</TD>
<TD WIDTH=200>
Which of these guys would you lend money to?<BR>
<INPUT TYPE=CHECKBOX NAME="Lend money?...Tom" VALUE="YES">
Tom <BR>
<INPUT TYPE=CHECKBOX NAME="Lend money?...Ricky" VALUE="YES">
Ricky <BR>
<INPUT TYPE=CHECKBOX NAME="Lend money?...Terry" VALUE="YES">
Terry<BR>
<INPUT TYPE=CHECKBOX NAME="Lend money?...BU" VALUE="YES">
Bunty<P>
</TD>
<TD WIDTH=199>
Which of these guys would you trust with your sister?<BR>
<INPUT TYPE=CHECKBOX NAME="Date sister?...Tom" VALUE="YES"> Tom
<BR>
<INPUT TYPE=CHECKBOX NAME="Date sister?...Ricky" VALUE="YES">
Ricky <BR>
<INPUT TYPE=CHECKBOX NAME="Date sister?...Terry" VALUE="YES">
Terry<BR>
<INPUT TYPE=CHECKBOX NAME="Date sister?...BU" VALUE="YES">
Bunty<P>
</TD>
</TR></TABLE>
</CENTER>
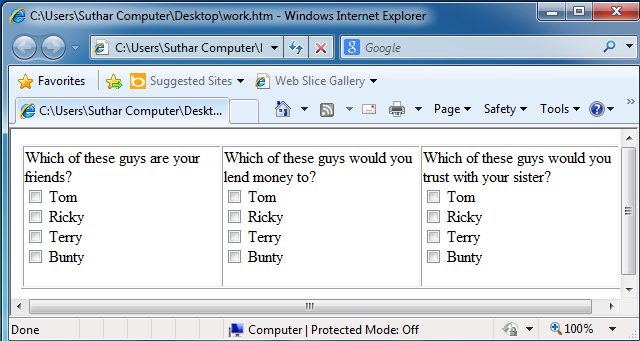
Figure: A Form on a Web Page with Checkboxes