There were 50 respondents to our survey.
The first component of the data examined here focuses on student's preference (ecommerce or traditional commerce).
The Second component of the data examined here focuses on the range of procedure's easiness.
Discussion
We were surprising with our survey's results. Most of people prefer e-commerce over traditional commerce, on the other hand most of them think of it as a hard procedure!
Pies Chart of Range of Student Preference
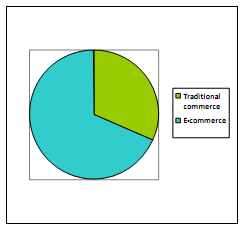
Figure Students' preference between e-commerce and traditional commerce
Pie Chart of Range of Procedure Easiness
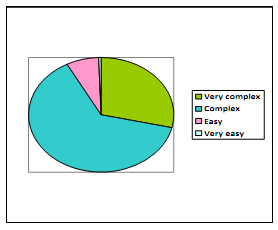
Figure Procedure's easiness of e-commerce
All this data leads us to the fact that the next decade will be an innovative and demanding one for e-commerce. Also, it indicates that there are some obstacles for some people, such as thinking of e-commerce as a complex procedure, or fearing of their privacy. And of course all people have fear of criminal hackers. According to these results, our job here is to define the whole aspects of e-commerce, focusing on these obstacles, aware people of them and how to handle these issues and make the procedure understandable and much easier for the readers.
Conclusion
These result and pre-work provided us a great opportunity to start our research with a right background, so we were able to explain the causes that lead to this quantitative information we got.