The 68Hc11 is actually a complex micro-controller its contains internally RAM, EEPROM, Parallel IO and serial ports, hardware timers and a 8 channel ADC. The internal structure is shown .A micro controller is only useful if the operator can communicate with the outside world, for this purpose the I/O devices have been included. The 68HC11 series of micro controllers have many I/O devices in their family, each devices has its own particular quirks. The different devices are appended by a letter denoted the series type
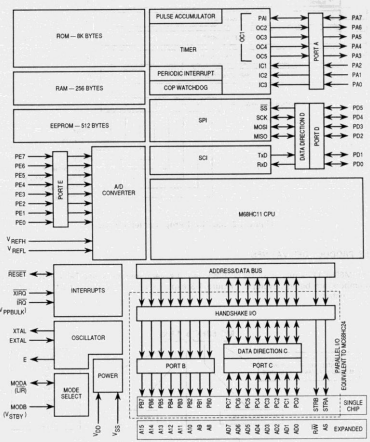
MC68HC11A0 5 ports, serial comms 256 byte RAM and 8 channel 8 Bit ADC
MC68HC11A1 5 ports, serial comms 256 byte RAM and 8 channel 8 Bit ADC 16 Timer and 512 byte EEPROM
MC68HC11A8 5 ports, serial comms 256 byte RAM and 8 channel 8 Bit ADC 16 Timerand 512 byte EEPROM 8K ROM
MC68HC11E1 5 ports, serial comms 512 byte RAM and 8 channel 8 Bit ADC 16 Timer and 512 byte EEPROM
MC68HC11E9 5 ports, serial comms 512 byte RAM and 8 channel 8 Bit ADC 16 Timer and 512 byte EEPROM 12K ROM
MC68HC11F1 6 ports, serial comms 1024 byte RAM and 8 channel 8 Bit ADC 16 Timer and 512 byte EEPROM
MC68HC11D3 5 ports, serial comms 256 byte RAM and 8 channel 8 Bit ADC 16 Timer and 512 byte EEPROM 4k One time PROM