Question
(a) Inspect the following ifconfig output of an IPv6 interface:
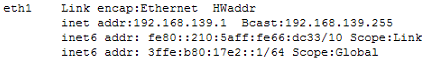
i. What is the hidden Hardware Address of the interface on Line #1?
ii. What is the hidden subnet mask on Line #2?
iii. What does /10 mean on line #3?
iv. Why does line #4 have /64?
(b) Consider that a host is sending a frame of 1500 bytes to another host found 10 kilometers away. determine the total latency (from the first bit transmitted by sending host to the last bit buffered by receiving host) on a 100 Base-FX Ethernet network with a "store-N-forward" switch in the path. Consider that the speed of light in a fiber-optic cable is 2 x 108ms-1and that the switch begins retransmitting immediately (i.e. switching delay is negligible) after it has finished buffering the frame completely.
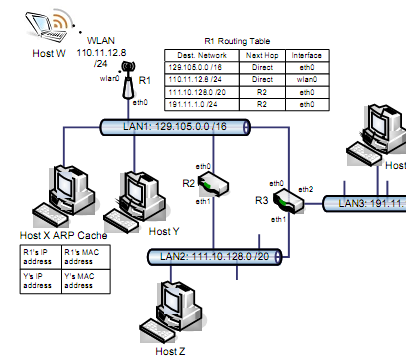
(c) Please refer to the Figure below and answer the following:
i. Consider Host X intend to transfer an IP datagram to Host Y, which is on the same LAN: LAN1 with network id 129.105.0.0 /16. Briefly explain the different interactions that take place by Host X at both the network layer and data-link layers for sending this datagram to Host Y. (The ARP cache of host X at that moment is shown above.)
ii. Suppose now that Host X wants to send a datagram to Host W, which is connected to an 802.11g router R1 via a wireless LAN (network id for this WLAN is 110.11.12.8 /24). Should Host X use ARP to query for Host W's MAC address?
iii. Suppose that router R1 is the default gateway for Host X, briefly describe the steps taken by Host X and R1 at both the network layer and data-link layer for sending a datagram to host W. (The routing table of R1 is shown above. Assume R1 has the MAC address of W in its ARP cache.)
iv. Host X now wants to send a datagram to Host Z on LAN 2 (network id: 111.10.128.0 /20). Assume that Host X has default gateway as R1. Describe the actions taken by R1 (and hence at R2) at both the network layer and data-link layer for routing this datagram to host Z.
v. Consider Host X intends to send another datagram to Host Z. Will Host X still send it to R1? Or will it send it to R2? Since Host X does not have R2's MAC address. Explian how Host X obtains R2's MAC address using the ARP protocol.