Requirements
You are required to program (in a high level language such as C, C++, Java) and implement a cache simulator which will have the following inputs and outputs:-
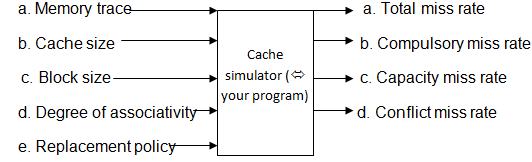
Memory trace ó smalltex.din (during code development microtex.din - see later) and each address is the current address, in RAM, of a Byte required by the CPU.
Cache size ó size of cache in bytes
Block size ó size of blocks in bytes
Degree of associativity ó direct (1-way), 2-way, 4-way, 8-way, and fully associative
Replacement policy ó Random and LRU are to be implemented.
Total miss rate = compulsory + capacity + conflict miss rates.
* The memory trace file (smalltex.din) is located at
/home/csiii/csiiilib/arc/smalltex.din or
/home/3rd/csiiilib/arc/smalltex.din
Copy this file to your arc directory where you will be running your assignment from.