QUESTION
a) Consider the speed of propagation of an electrical signal is same to 2x108m/s, evaluate the ratio of the propagation delay to the transmit time for the given types of data link and 1000 bytes of data.
i) 100 m of UTP cable at a transmission rate of 1 Mbps
ii) 2.5 km of coaxial cable and transmission rate of 10 Mbps
iii) A geostationary satellite VSAT link and a transmission of 512 kbps.
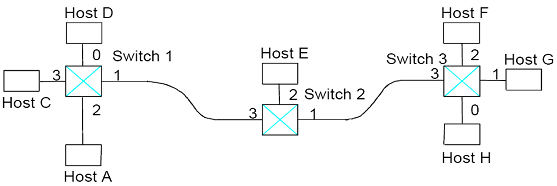
b) Consider the arrangement of self-learning switches given in the figure below. Consider all forwarding table are initially empty, provide the forwarding tables for each of the 3 switches after the subsequent consecutive transmissions:
i) Host A to Host F
ii) Host C to Host G
iii) Host E to Host H
iv) Host D to Host E
c) The ASN.1 specification language is an integral part of the OSI Reference Model architecture, and is used in some protocols on the Internet. ASN.1 data objects are encoded for transmission using the Basic Encoding Rules. Provide an example of a transmitted byte-stream in hexadecimal by using the subsequent module of data type declarations and its corresponding instances:
name ::= OCTET STRING
number ::= INTEGER
active ::= BOOLEAN
{name, "Stevie G"}
{number, 8}
{active, 1}
d) In relation to network management, explain the following terms:
i) SNMPv1 Trap message
ii) Management Information Base.
e) In respect to wireless network,
i) Give one advantage of using IEEE 802.11a over the other flavours.
ii) Give one advantage of using IEEE 802.11g over the other flavours.
iii) Describe how Frequency Hopping Spread Spectrum works in relation to Bluetooth.
iv) Consider that you have a wireless access point that is using WEP, explain two ways in which you could make your wireless network more secure.