Reference no: EM131998598
Question 1. Alice and Bob, are communicating in the presence of an adversary (attacker with malicious intent) Eve. For symmetric encryption algorithms they use openssl and for public key algorithms they use gpg. For the following set of cryptographic functions and the specified message:
- Message m: "Alice owes Bob 100 AUD" (without the quotation marks)
- h(): SHA256
- E(): AES-128-CTR when symmetric, RSA when asymmetric
- || : Concatenation
KAB: Shared secret key between Alice and Bob for symmetric key algorithm with hex value
0123456789ABCDEF0123456789ABCDEF
IV : The Initialisation Vector for CTR algorithm with hex value
FFEEDDCCBBAA998877665544332211
- P UA: Public key of Alice (Alice.pub file)
- P RA: Private key of Alice (Alice.prv file)
- P UB: Public key of Bob (Bob.pub file)
- P RB: Private key of Bob (Bob.prv file)
Note: All of the key files are included in FIT2093-AssignmentFiles.zip (link provided in guidlines). The message is also included in the compressed file as plain.txt.
For each of the following protocols:
(a) Alice → Bob : m||h(m)
(b) Alice → Bob : E(P UB, m)
(c) Alice → Bob : m||E(P RA, h(m))
(d) Alice → Bob : E(KAB, m||h(m))
i) Specify whether each of the following security services are provided and explain why or why not:
- confidentiality;
- integrity;
- authenticity; and
- non-repudiation.
ii) Produce and report:
- the hex value of the protocol message;
- the commands used; and
- in case a security service is not provided, show with an example how an attack is performed.
[40 Marks]
2. Adam is using CFB mode of operation to encrypt a 256-byte file to send it to Beatrice.
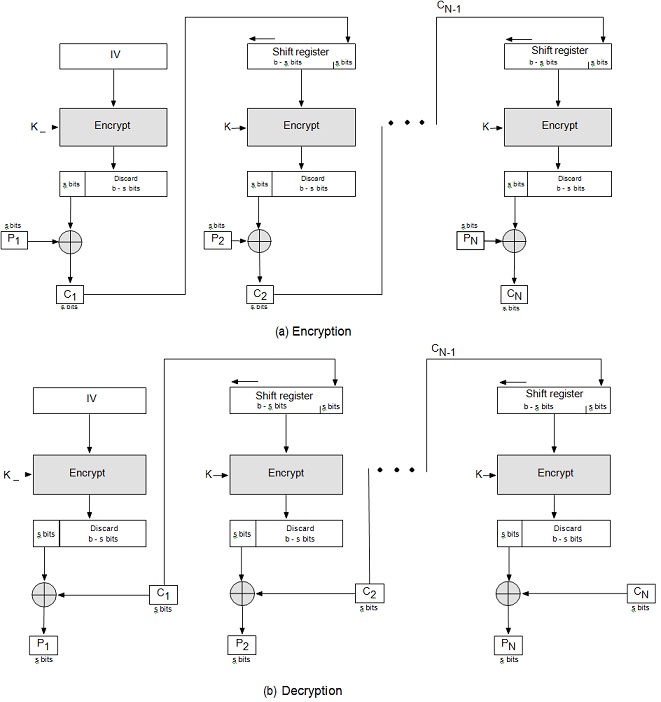
Figure 1: s-bit Cipher Feedback Mode of Operation Using openssl show with example:
(a) If there is an error in transmitted ciphertext block C1, how many plaintext blocks will be corrupted when Beatrice decrypts the file for 8-bit CFB-DES?
(b) If there is an error in transmitted ciphertext block C1, how many corrupted plaintext blocks when 8-bit CFB-AES is used?
(c) If there is a change in source plaintext block P1, how many ciphertext blocks will be affected if 8-bit CFB-DES is used? How many blocks if 8-bit CFB-AES is used?
(d) If there is a change in source plaintext block P1, for both CFB-DES and CFB-AES explain the effect at reciever.
Note:
Use the provided sample file cfb.txt in assignment compressed file
FIT2093-AssignmentFiles.zip (the link is provided in guidlines page).
- For DES algorithm use FEDCBA9876543210 as the key and 0011223344556677 as the IV. For AES algorithm use FEDCBA9876543210FEDCBA9876543210 as the key and
00112233445566778899AABBCCDDEEFF as the IV.
3. Joe is an overworked and under-appreciated programmer at "This Secure World" company. He is asked to write an RSA key generation algorithm that performs better than the competition. To increase the efficiency of his algorithm he decides instead of generating two random prime factors for the modulus part of every RSA key pair, to reuse one of the previous factors and only generate one new random prime number for the new pair. For instance, RSA moduli (n values) generated by Joe's algorithm would be of the form::
n1 = p1 × q1
n2 = p2 × q1
n3 = p2 × q2
n4 = p3 q2
. . .
This has increased the efficiency of his algorithm by reducing the time required to test the primality of the randomly generated numbers and for the first time in quite a while he is praised by his supervisor for the surprisingly good performing algorithm. The company is going to embed this algorithm in all of their hardware and software products. You are tasked with evaluation of the security of Joe's approach by either approving or rejecting Joe's idea. You are given 20 public keys (modulus n) where some are generated using Joe's algorithm and others using a different algorithm. For all 20 samples, the value of e is 65537. Also, encryptions of 20 randomly generated plaintexts with respect to each public key are provided (c values in sample file).
If you accept Joe's idea, first clearly state it. Then, you must explain in detail why his method is secure and why the plaintexts cannot be recovered.
If you reject Joe's idea, first clearly state it. Then, you must demonstrate in detail how you can recover the plaintexts for keys generated using Joe's algorithm. Also, provide all the recovered plaintexts in decimal format (base 10).
Note:
- All numbers are represented in decimal (base 10).
*only task 3