Reference no: EM131084145
Write a function N=countequal(G,T) that duplicates the action of hist(G,T) in Example 1.47.
Example 1.47
Simulate the testing of 100 microprocessors as described in Example 1.43. Your output should be a 4 × 1 vector X such that Xi is the number of grade i microprocessors.
Example 1.43
Keep in mind that by the extended definition of the multinomial coefficient, P[S v, f,m] is nonzero only if v, f , and m are nonnegative integers such that v + f + m = 100. Continuingwith Example 1.37, suppose in testing a microprocessor that all four grades have probability 0.25, independent of any other microprocessor. In testing n = 100 microprocessors, what is the probability of exactly 25 microprocessors of each grade?
Example 1.37
A chip fabrication facility produces microprocessors. Each microprocessor is tested and assigned a grade s ∈ S = {s0,...,s3}. A grade of sj indicates that the microprocessor will function reliably at a maximum clock rate of sj megahertz (MHz). In testing 10 microprocessors, we use xi to denote the grade of the ith microprocessor tested. Testing 10 microprocessors, for example, may produce an observation sequence
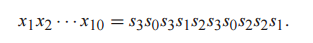
|
How much would be needed for a misdemeanor charge
: Did you have probable cause to approach the defendant while he was parked at the traffic light? Why or why not? Defend your answer - Do you feel that the entrapment defense is a valid one, considering the assignment scenario? Why or why not? Defend..
|
|
What is the probability p[g = r]
: what is the probability P[G = R]?
|
|
Formulation of the ethical question
: Present a revised formulation of the ethical question and introduction to the topic. Explain the kind of reasoning you think is the best way to approach this question, and how that reasoning supports the position you think is strongest.
|
|
An ordinary random sum of random variables
: Suppose we flip a fair coin repeatedly. Let Xi equal 1 if flip i was heads (H) and 0 otherwise. Let N denote the number of flips needed until H has occurred 100 times.
|
|
Write a function n=countequal(g,t) that duplicates
: Simulate the testing of 100 microprocessors as described in Example 1.43. Your output should be a 4 × 1 vector X such that Xi is the number of grade i microprocessors.
|
|
Passes mcnabb throws in a game
: In any game, the number of passes N that Donovan McNabb will throw has a Poisson distribution with expected value µ = 30. Each pass is a completed with probability q = 2/3, independent of any other pass or the number of passes thrown.
|
|
Type of literature piece
: Introduction: Includes a greeting, purpose of the oral presentation, the type of literature piece you will be presenting, and three main points (subtopics) of your piece.
|
|
Discover about bonzo and stilson
: Why does Ender cry after the fight with Bonzo? What do we discover about Bonzo and Stilson? Are you surprised?
|
|
Input the stated items into an excel spreadsheet
: Create a pie chart to show the distribution of costs for the items you purchased.
|